Cloud Security-Scope, Threats, Solutions, limitations
Cloud security is a sub-field of cyber-security that specifically focuses on securing cloud computing systems.

In today’s digital age, organizations of all sizes are adopting cloud computing to store and process their data. Cloud computing provides a cost-effective and efficient way to manage and store data.
However, with the benefits of cloud computing come several risks, including security threats. Cloud security is the protection of data, applications, and infrastructure that are involved in cloud computing from unauthorized access, use, disclosure, and modification.
Scientists have surveyed cloud security issues, authentication schemes, data storage tech, and explored the use of Artificial Neural Networks (ANNs) in securing data on the cloud. [1]
Key Points
- Cloud computing is a cost-effective and efficient way to manage and store data, but it comes with security threats.
- Cloud security pertains to safeguarding cloud computing systems, including data, applications, and infrastructure, against any unauthorized use, access, disclosure, or modification.
- The history of cloud security dates back to the 1960s, and cloud security became a significant concern in the mid-2000s due to high-profile data breaches.
- The scope of cloud security includes network security, data security, application security, identity and access management, compliance management, cloud security governance, and cloud security services.
- Cloud security tools include firewalls, intrusion detection and prevention systems, antivirus and antimalware software, encryption software, identity and access management solutions, and security information and event management tools.
- Common cloud security threats include data breaches, insider threats, malware and viruses, DDoS attacks, account hijacking, and insecure APIs.
In this article we will discuss cloud security, history of cloud security, tools, threats, types, services, importance, applications, limitations, challenges, and solutions. Which will be very beneficial for you.
Cloud Security Examples
Cloud security examples include Amazon Web Services (AWS) security, Microsoft Azure security, Google Cloud Platform (GCP) security, and Oracle Cloud security.
These cloud service providers offer various security features, such as access control, identity and access management, data encryption, network security, threat detection and prevention, and compliance management.
History of Cloud Security
The concept of cloud security introduced in 1960s, when computer scientist John McCarthy introduced the idea of timesharing.
In the 1970s, researchers at Xerox PARC developed the first virtual machine, which paved the way for cloud computing.
In the 1990s, the term “cloud” was coined, and the first cloud service providers, such as Sales force and Amazon, emerged.
However, it wasn’t until the mid-2000s that cloud security became a significant concern due to several high-profile data breaches.
Scope of Cloud Security
The scope of cloud security is vast and encompasses various aspects of cloud computing. Cloud security involves securing the cloud infrastructure, applications, and data from security threats and ensuring compliance with regulatory requirements and industry standards.
The following are some of the areas included in the scope of cloud security:
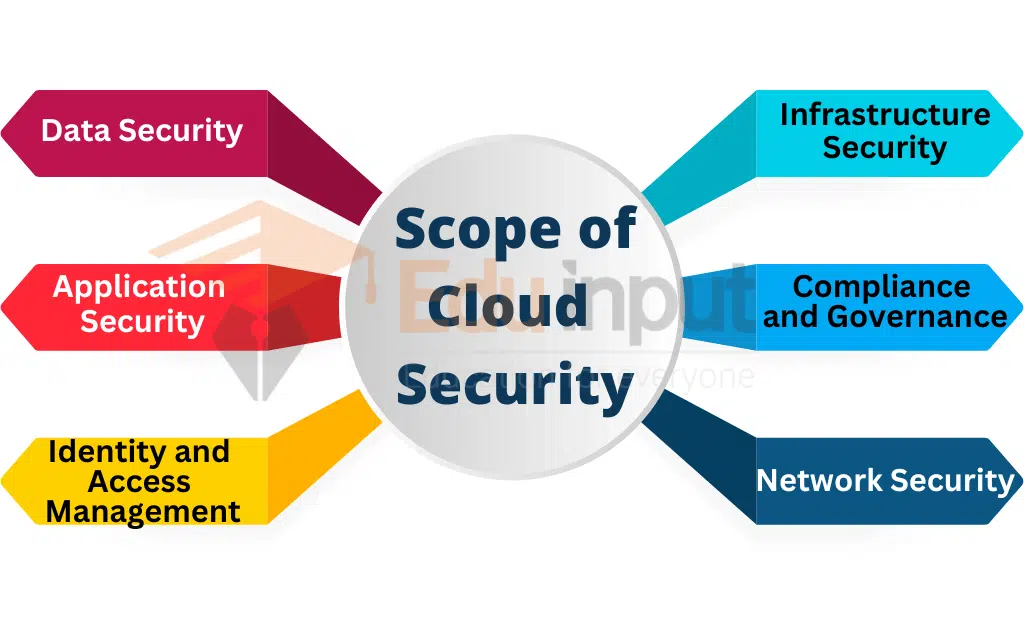
Network Security: Network security is an essential aspect of cloud security that involves securing the cloud infrastructure, including the network, routers, switches, and firewalls.
Network security solutions include intrusion detection and prevention systems (IDS/IPS), virtual private networks (VPNs), and firewalls.
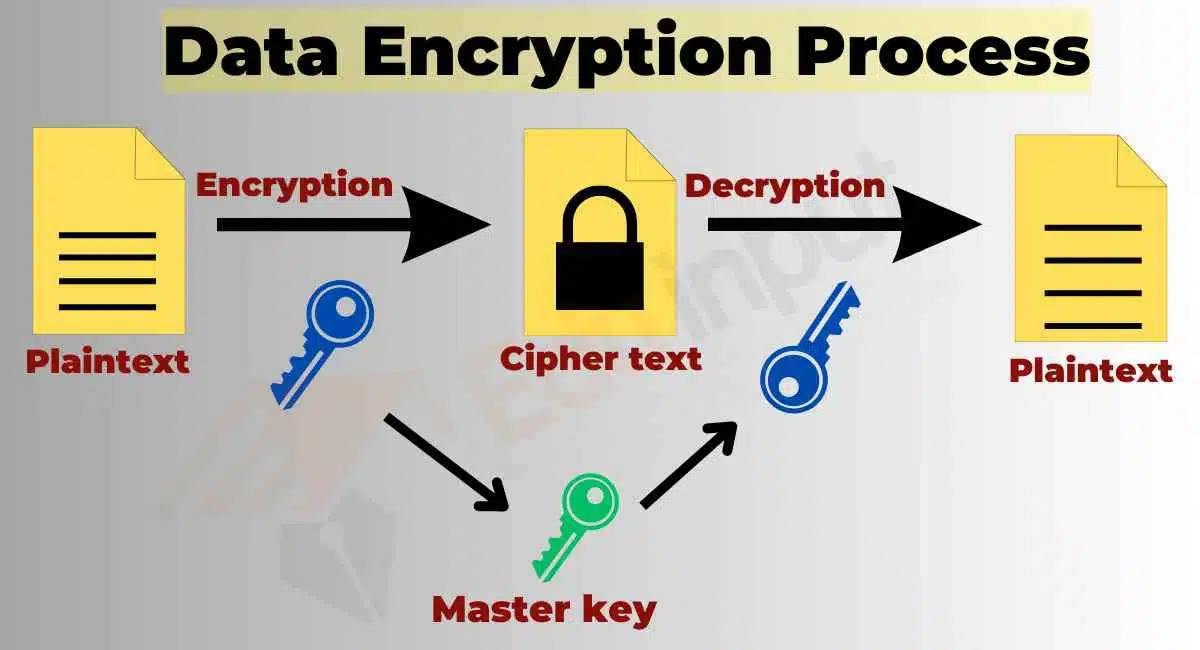
Data Security: Data security involves protecting data stored in the cloud from unauthorized access, use, disclosure, and modification. Data security solutions include data encryption, access controls, and data loss prevention (DLP) solutions.
Application Security: Application security involves securing applications hosted in the cloud from security threats such as malware, viruses, and other cyberattacks. Application security solutions include web application firewalls (WAFs), vulnerability scanners, and code reviews.
Identity and Access Management: Identity and access management (IAM) involves managing user identities, roles, and access privileges in the cloud. IAM solutions include multi-factor authentication (MFA), single sign-on (SSO), and role-based access control (RBAC).
Compliance Management: Compliance management involves ensuring compliance with regulatory requirements and industry standards related to cloud security, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS). Compliance management solutions include compliance monitoring and auditing tools.
Cloud Security Governance: Cloud security governance involves establishing policies, procedures, and controls to manage cloud security risks effectively. Cloud security governance solutions include risk management frameworks, security awareness training, and security incident response plans.
Cloud Security Services: Cloud security services are services provided by cloud service providers to enhance the security of the cloud infrastructure, applications, and data. Cloud security services include managed security services, cloud access security brokers (CASBs), and security information and event management (SIEM) solutions.
Cloud Security Tools
Cloud security tools include firewalls, intrusion detection and prevention systems (IDS/IPS), antivirus and antimalware software, encryption software, identity and access management (IAM) solutions, and security information and event management (SIEM) tools. These tools help organizations monitor and protect their cloud resources from security threats.
Cloud Security Threats
Cloud security threats are a major concern for organizations that use cloud computing services. The following are some of the most common cloud security threats:
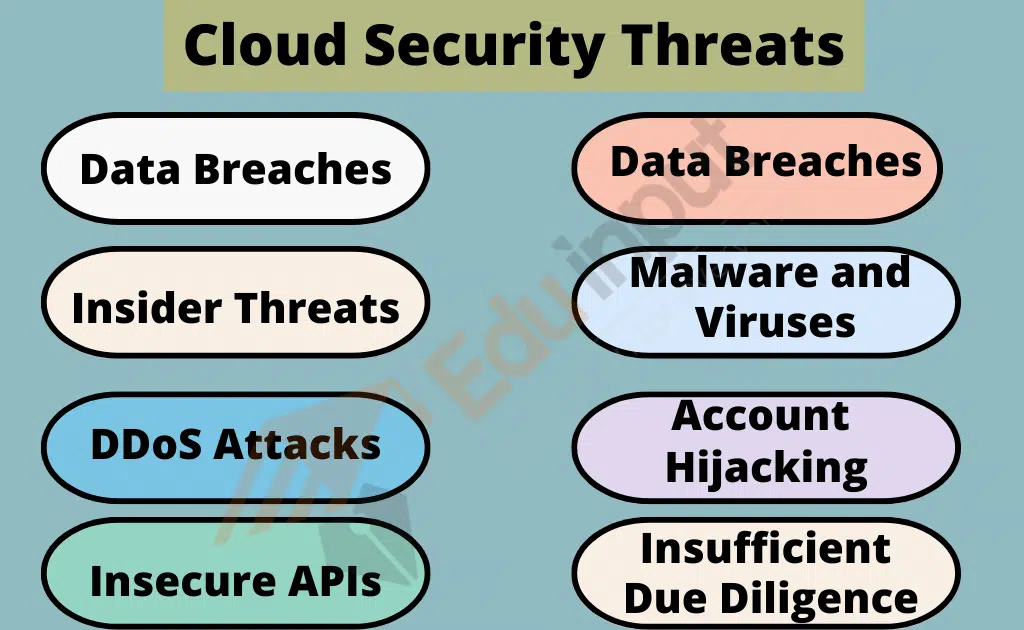
Data Breaches: A data breach is a security incident in which an unauthorized party gains access to sensitive data stored in the cloud. Data breaches can occur due to weak authentication and access controls, vulnerabilities in cloud applications, and insecure APIs. Data breaches can lead to financial loss, reputational damage, and legal liabilities.
Insider Threats: Insider threats refer to security risks posed by individuals within an organization, such as employees, contractors, and business partners. Insider threats can be intentional or unintentional and can result in data theft, data manipulation, and other security incidents. Insider threats can be mitigated through access controls, security awareness training, and monitoring user activity.
Malware and Viruses: Malware and viruses are malicious software programs that can infect cloud applications and data. Malware and viruses can be introduced into the cloud through phishing attacks, email attachments, and infected websites. Malware and viruses can cause data loss, data corruption, and other security incidents.
DDoS Attacks: Distributed denial-of-service (DDoS) attacks are cyberattacks in which an attacker attempts to disrupt the availability of a cloud service by flooding it with traffic. DDoS attacks can be carried out through botnets, which are networks of compromised devices. DDoS attacks can cause service downtime, loss of revenue, and reputational damage.
Account Hijacking: Account hijacking is a security incident in which an attacker gains access to a cloud user’s account through stolen credentials or other means. Account hijacking can be used to steal data, launch further attacks, or cause other security incidents. Account hijacking can be mitigated through strong authentication and access controls.
Insecure APIs: Application Programming Interfaces (APIs) are used to connect cloud applications and services. Insecure APIs can be exploited by attackers to gain unauthorized access to data and applications, manipulate data, and launch further attacks. Insecure APIs can be mitigated through secure coding practices, API testing, and monitoring.
Insufficient Due Diligence: Insufficient due diligence refers to a lack of proper investigation and risk assessment before choosing a cloud service provider. Insufficient due diligence can lead to selecting an insecure cloud service provider, which can result in security incidents and data breaches. Due diligence can be enhanced through careful vendor selection, risk assessment, and contract negotiation.
Cloud security involves protecting cloud resources, including data, applications, and infrastructure, from a range of threats. There are various types of cloud security that organizations must consider to ensure the security of their cloud resources. The following are some of the most important types of cloud security:
Data Security: Data security involves protecting sensitive data stored in the cloud from unauthorized access, disclosure, or modification. Data security measures include encryption, access controls, and data classification.
Encryption is the process of converting data into a coded form to protect it from unauthorized access. Access controls limit access to data based on user identity and permissions, while data classification categorizes data based on its sensitivity level.
Application Security: Application security involves protecting cloud applications from security threats such as malware, viruses, and cyberattacks. Application security measures include secure coding practices, penetration testing, and vulnerability assessments. Secure coding practices involve writing code that is resistant to security threats, while penetration testing and vulnerability assessments test the security of cloud applications and identify potential vulnerabilities.
Infrastructure Security: Infrastructure security involves protecting the cloud infrastructure, including servers, networks, and storage, from security threats. Infrastructure security measures include network segmentation, firewall protection, and intrusion detection systems.
Network segmentation involves dividing the cloud network into smaller segments to limit the scope of security incidents, while firewall protection and intrusion detection systems monitor network traffic for security threats.
Identity and Access Management: Identity and access management (IAM) involves managing user identities and permissions to access cloud resources. IAM measures include multifactor authentication, single sign-on, and role-based access controls. Multifactor authentication requires users to provide multiple forms of identification, such as a password and a fingerprint, to access cloud resources. Single sign-on enables users to access multiple cloud applications with a single set of login credentials, while role-based access controls limit access to cloud resources based on user roles and permissions.
Compliance and Governance: Compliance and governance involve ensuring that cloud resources comply with regulatory requirements and organizational policies.
Compliance and governance measures include regular security audits, policy enforcement, and incident response planning. Security audits evaluate the effectiveness of cloud security measures, while policy enforcement ensures that cloud resources comply with organizational policies and regulatory requirements.
Incident response planning involves developing procedures to respond to security incidents effectively.
Cloud Security Services
Cloud security services include Infrastructure as a Service (IaaS) security, Platform as a Service (PaaS) security, Software as a Service (SaaS) security, and Security as a Service (SecaaS). IaaS security involves securing the cloud infrastructure, including the physical servers, storage devices, and network connections. PaaS security involves securing the cloud platform, including the operating system, middleware, and runtime environment. SaaS security involves securing the cloud applications, including the data, code, and configuration. SecaaS involves outsourcing security services to a third-party provider.
Importance of Cloud Security
The importance of cloud security cannot be overstated. Cloud security helps organizations protect their sensitive data, maintain business continuity, and comply with regulatory requirements and industry standards. Cloud security also helps organizations reduce the risk of security threats and minimize the impact of security incidents.
Applications of Cloud Security
Cloud security has several applications, including:
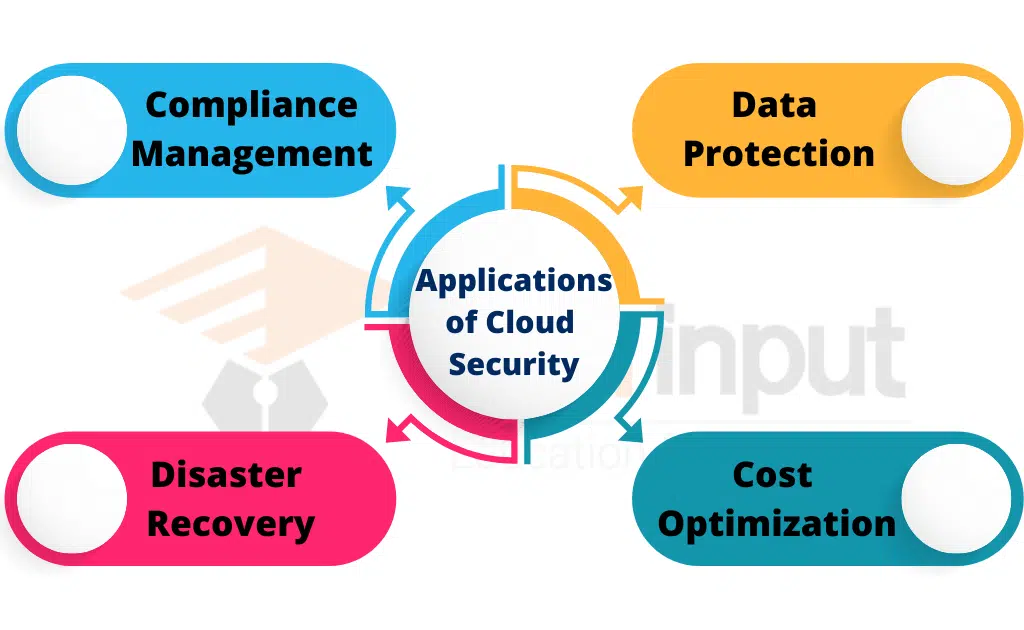
Data Protection: Cloud security ensures the confidentiality, integrity, and availability of data stored in the cloud. It also helps organizations meet regulatory requirements and industry standards related to data protection.
Compliance Management: Cloud security helps organizations comply with various regulations and standards, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS).
Disaster Recovery: Cloud security helps organizations ensure business continuity by providing disaster recovery solutions. Cloud-based disaster recovery solutions allow organizations to recover their data and applications in the event of a disaster.
Cost Optimization: Cloud security helps organizations optimize their costs by providing scalable and cost-effective security solutions. Cloud-based security solutions allow organizations to pay for only what they use, reducing their overall security costs.
Limitations of Cloud Security
Despite its benefits, cloud security has several limitations, including:
Limited Control: Cloud security limits the control that organizations have over their data and applications. Cloud service providers are responsible for securing the cloud infrastructure, which means that organizations have limited control over the security measures that are implemented.
Shared Responsibility: Cloud security is a shared responsibility between the organization and the cloud service provider. This means that organizations must ensure that their data and applications are secure, even though they are hosted in the cloud.
Compliance Challenges: Cloud security can create compliance challenges for organizations. Different regulations and standards may have different requirements for cloud security, making compliance a complex and challenging process.
Cloud Security Challenges
Cloud security faces several challenges, including:
Lack of Awareness: Many organizations are not aware of the security risks associated with cloud computing. This lack of awareness can lead to security breaches and data loss.
Complexity: Cloud security can be complex due to the different types of cloud services and the various security threats that exist.
Compliance: Compliance with regulatory requirements and industry standards can be a challenge for cloud security, as different regulations may have different requirements for cloud security.
Cloud Security Solutions
To address these challenges, organizations can implement various cloud security solutions, such as:
Access Control: Access control solutions, such as IAM, can help organizations control user access to cloud resources and prevent unauthorized access.
Encryption: Encryption solutions can help organizations protect their data from unauthorized access by encrypting it while it is in transit and at rest.
Threat Detection and Prevention: Threat detection and prevention solutions, such as IDS/IPS and SIEM, can help organizations detect and prevent security threats in the cloud.
Compliance Management: Compliance management solutions, such as compliance monitoring and auditing tools, can help organizations ensure compliance with regulatory requirements and industry standards.
Related FAQs
What are the four areas of cloud security?
The four areas of cloud security are network security, data security, application security, and identity and access management.
What is the objective of cloud security?
The objective of cloud security is to protect data, applications, and infrastructure that are involved in cloud computing from unauthorized access, use, disclosure, and modification.
How many layers are there in cloud security?
There are three layers in cloud security: the physical layer, the virtualization layer, and the application layer.




Leave a Reply