Cyber Security- Types, Threats, and Certifications
Cyber security means protecting computers, phones, and other electronic devices, as well as networks and data, from unauthorized users who want to do harm.
They might want to steal, change, or delete important information, demand money using scary tactics, or mess up normal computer activities. Cyber security is all about stopping these Criminals and keeping everything safe.

Why is Cyber Security important?
Cyber security is important because it helps to protect our personal and business information from being stolen or damaged by cybercriminals. As technology is widely used in our daily lives, we are more vulnerable to cyber attacks than ever before.
A successful cyber attack can result in the loss of sensitive data, financial losses, reputational damage, and legal liability. By implementing strong cyber security practices, we can prevent our online activities and protect our digital assets from potential harm.
Different Types of Cybersecurity
There are different types of cybersecurity measures that can be taken to protect against cyber threats. Here are some common types of cybersecurity:
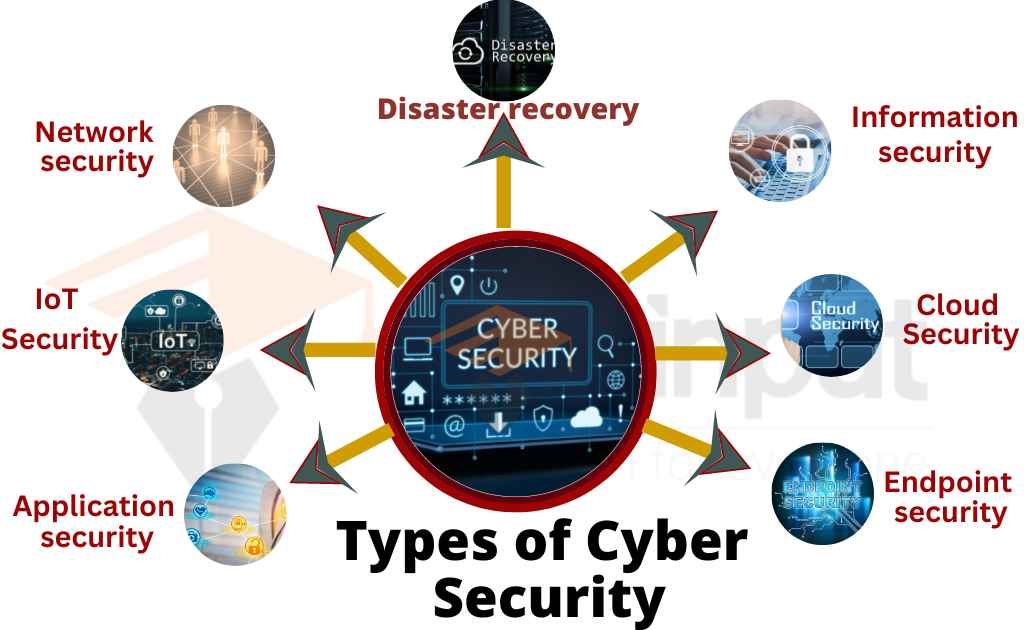
Network security
This involves securing computer networks from unauthorized access, intrusion, and malware attacks.
IoT Security
The Internet of Things (IoT) is becoming increasingly popular. IoT refers to the connection of various devices, such as smartphones, laptops, and home appliances, to the internet. This connection enables us to enjoy many conveniences, but it also comes with certain risks.
Endpoint security
This involves securing individual devices such as laptops, smartphones, and other internet-enabled devices from cyber attacks.
Application security
This involves securing applications and software from being exploited or hacked by attackers.
Information security
This involves protecting sensitive information from being accessed by unauthorized users or from being disclosed to malicious entities.
Cloud Security
This involves securing cloud-based data and systems from unauthorized access, cyber-attacks, and other threats.
Disaster recovery and business continuity
This involves planning for the worst-case scenarios and ensuring that critical systems can be restored in the event of a cyber attack.
By implementing these different types of cyber security measures, individuals and organizations can better protect their digital assets and sensitive information from cyber threats.
Types of cyber security threats
Cybersecurity threats are becoming more and more common as our world becomes more connected digitally. Some of the most common types of cybersecurity threats are:
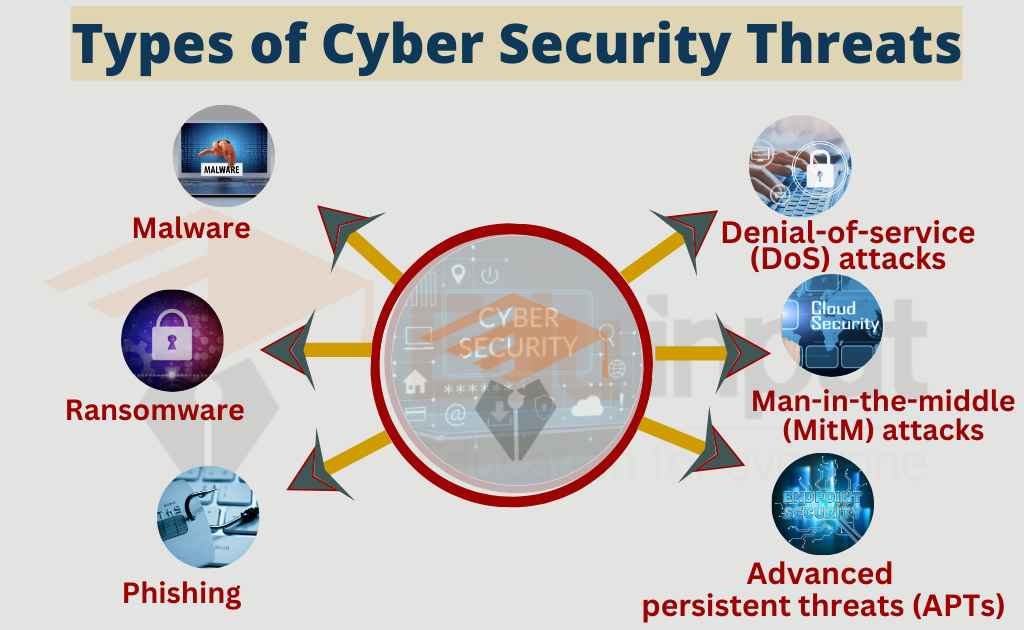
Malware
Malware is a type of malicious software that can harm your computer or mobile device. Malware includes things like spyware, ransomware, viruses, and worms.
It usually gets into your system when you click on a malicious link or download untrustworthy software. Once it’s in your system, it can collect your sensitive information, manipulate your network, or even destroy your data.
It’s important to be cautious when clicking on links or downloading software to avoid getting malware on your device.
Ransomware
Ransomware is a type of malware that locks down your computer or files until you pay a ransom to the attacker. This can be a costly and time-consuming problem.
Phishing
Phishing is a type of social engineering attack that aims to trick people into giving away sensitive information, such as passwords or credit card numbers. This is often done through fake emails or websites that look legitimate.
Denial-of-service (DoS) attacks
DoS attacks are designed to overload a network or server, making it unavailable to legitimate users. This can disrupt business operations or shut down a website entirely.
Man-in-the-middle (MitM) attacks
MitM attacks occur when an attacker intercepts communication between two parties to steal information or manipulate the conversation.
Advanced persistent threats (APTs)
APTs are long-term, targeted attacks that are often used by state-sponsored actors or cybercriminals to steal sensitive data or intellectual property.
It’s important to be aware of these types of cybersecurity threats and take steps to protect yourself and your devices. This can include using antivirus software, keeping your software up-to-date, and being cautious when opening emails or visiting websites.
Cyber Security Certifications
Here are some cyber security certifications which are given in below table:
| Certification | Certification Body | Level | Description |
| CompTIA Security+ | CompTIA | Entry | A vendor-neutral certification that covers network security, cryptography, threats and vulnerabilities, access control, and identity management |
| Cisco Certified Network Associate Security (CCNA Security) | Cisco | Entry | A certification that validates knowledge of securing Cisco networks and covers firewall technologies, security threats, VPNs, and intrusion prevention |
| Certified Information Systems Security Professional (CISSP) | International Information Systems Security Certification Consortium (ISC)² | Intermediate | A certification that focuses on the eight domains of information security, including security and risk management, asset security, security architecture, and software development security |
| Certified Ethical Hacker (CEH) | International Council of E-Commerce Consultants (EC-Council) | Intermediate | A certification that covers ethical hacking techniques, such as footprinting and reconnaissance, scanning networks, enumeration, and system hacking |
| Certified Information Security Manager (CISM) | Information Systems Audit and Control Association (ISACA) | Advanced | A certification that focuses on information security governance, risk management, program development and management, and incident management |
| Certified Information Systems Auditor (CISA) | Information Systems Audit and Control Association (ISACA) | Advanced | A certification that covers auditing, control, and security of information systems, as well as governance and management of IT |
It is important to note that this table is not exhaustive and there are many other cybersecurity certifications available, each with its own unique focus and requirements. It is important to research and selects a certification that aligns with your career goals and interests.
Cyber Security Career Opportunities
There are numerous career paths available in cybersecurity, ranging from entry-level positions to senior-level roles. Some of the most common cybersecurity positions include:
Information Security Analyst: This role involves analyzing security measures, assessing potential risks, and implementing security solutions to safeguard an organization’s data.
Cybersecurity Consultant: A consultant works with clients to identify and address security risks, develop security plans, and implement security measures.
Penetration Tester: Also known as an ethical hacker, this professional is responsible for finding vulnerabilities in computer systems, networks, and applications to identify potential security risks.
Security Architect: This role involves designing, building, and implementing secure computer systems and networks.
Chief Information Security Officer (CISO): This is a senior-level role responsible for developing and implementing an organization’s cybersecurity strategy, policies, and procedures.
Related FAQs
Is cyber security a good career?
Yes, cybersecurity is a rapidly growing field and a good career choice for those interested in technology and security. With the increasing use of technology and the internet, there is a growing need for cybersecurity professionals to protect networks, systems, and data from cyber-attacks.
How do I start a career in cybersecurity?
To start a career in cybersecurity, you can pursue a degree or certification in cybersecurity, computer science, or a related field. You can also gain hands-on experience through internships, volunteering, or participating in cybersecurity competitions. Networking with professionals in the field and staying up-to-date on industry trends and best practices can also be helpful.
Is cyber security high paying?
Yes, cybersecurity is generally a high-paying field, particularly for those with experience and specialized skills. Salaries can vary depending on factors such as location, industry, and job title.
Which field is best in cyber security?
There are many different fields within cybersecurity, each with its own set of skills and job responsibilities. Some popular fields within cybersecurity include network security, application security, cloud security, incident response, and risk management.





Leave a Reply