Network Security – Protections and benefits
Network Security involves taking steps to protect a computer network and its information from being accessed, attacked, or harmed by harmful individuals or software, like hackers, viruses, and other potential threats.
It is the most important type of cyber security.
Scientists have explored various fields within the broad topic of network security, which encompasses security policy issues for both networks and computers, cryptography, and design and configuration issues for system security. Additionally, practical aspects like intrusion detection, traffic analysis, and network monitoring are important components of network security.[1]

Key Points
- Network security protects against harmful software and individuals, like hackers and viruses.
- Security measures: firewalls, antivirus software, intrusion detection/prevention systems, VPNs, access control, encryption, and email security.
- Benefits of network security: protection against cyber threats, business continuity, sensitive information protection, regulatory compliance, improved network performance, and cost reduction.
- Implementing network security measures reduces cyber-attack risk and protects valuable assets.
- Implementing network security measures helps protect valuable assets, like sensitive data and information, and reduces the risk of cyber-attacks.
In this article, we will discuss some of the most common types of network security protections, and the benefits of network security. Which will be very helpful for you.
Types of Network Security Protections
Network security is the practice of protecting computer networks and their associated systems, hardware, software, and data from malicious attacks, unauthorized access, and other security threats.
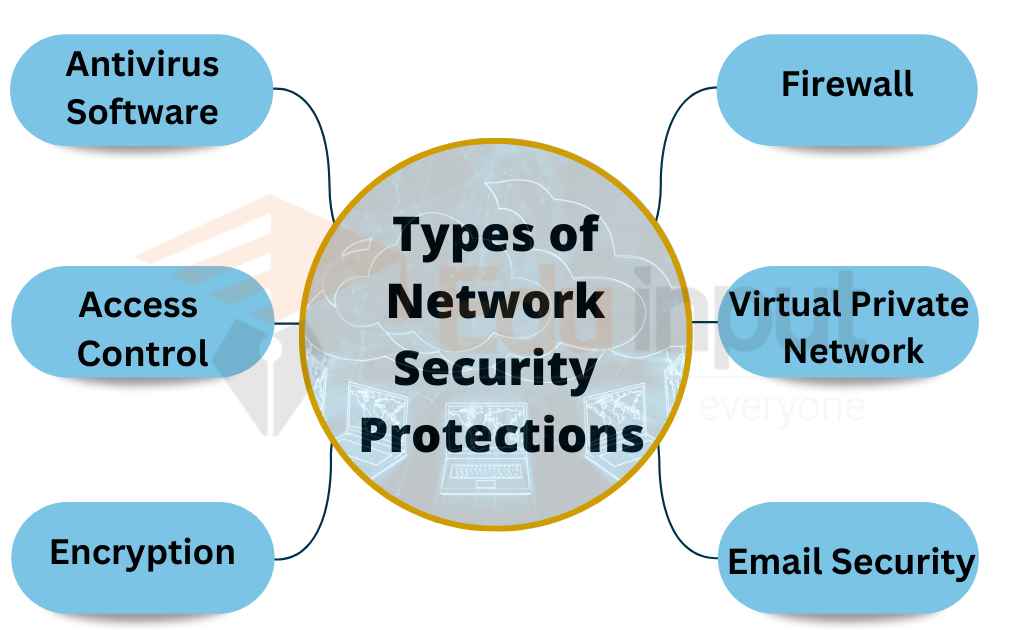
There are various types of network security protections that can be implemented to safeguard computer networks from cyber threats.
Firewall
A firewall is a network security system that monitors and controls incoming and outgoing network traffic. It acts as a barrier between an internal network and external networks, such as the internet.
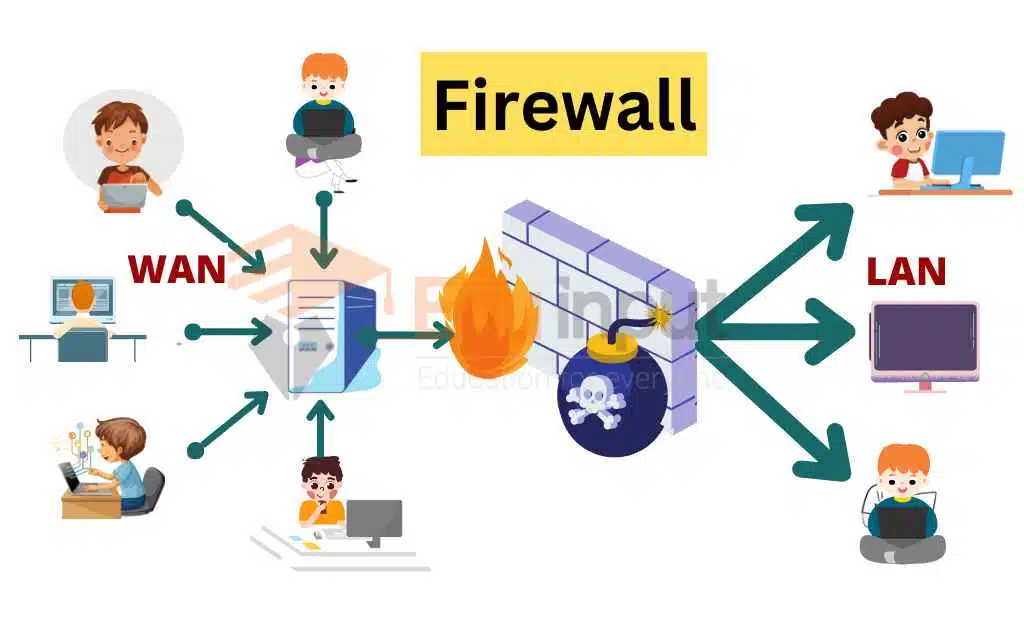
Firewalls can be hardware-based or software-based and can be configured to allow or block specific types of traffic based on predefined rules. A properly configured firewall can prevent unauthorized access to a network and protect against various types of cyber-attacks.
Antivirus Software
Antivirus software is a type of security software that is designed to detect and remove malware from a computer or network.
Malware, or malicious software, includes viruses, worms, Trojans, spyware, and other types of harmful software that can damage a computer or network.

Antivirus software can scan files and programs for malware and can also provide real-time protection against new and emerging threats.
Intrusion Detection and Prevention System
An intrusion detection and prevention system (IDPS) is a network security technology that monitors network traffic for signs of malicious activity.
IDPS can detect various types of attacks, including denial of service attacks, port scanning, and other network-based attacks. IDPS can also block or mitigate attacks in real time, providing an additional layer of protection against cyber threats.
Virtual Private Network
A virtual private network (VPN) is a secure connection between a remote device and a private network. VPNs are commonly used to provide remote access to corporate networks, enabling employees to work from home or while traveling.
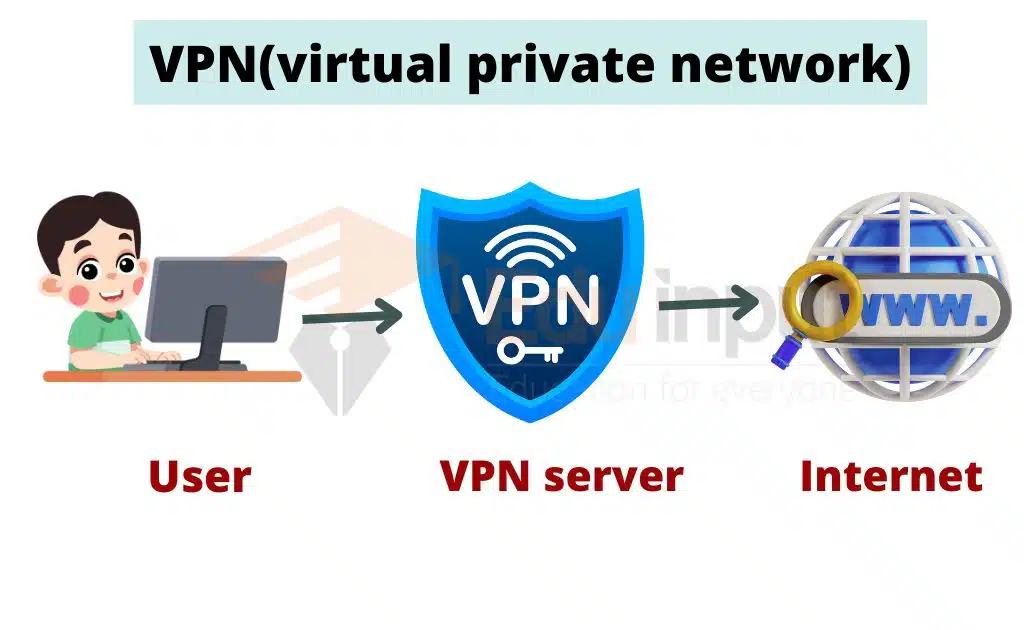
VPNs use encryption and other security technologies to ensure that data transmitted over the network is protected from interception and unauthorized access.
Access Control
Access control is a network security method that restricts access to network resources based on predefined policies.
Access control can be implemented using a variety of methods, such as usernames and passwords, biometric authentication, or smart cards. Access control can prevent unauthorized access to network resources, protecting sensitive data and other assets from cyber threats.
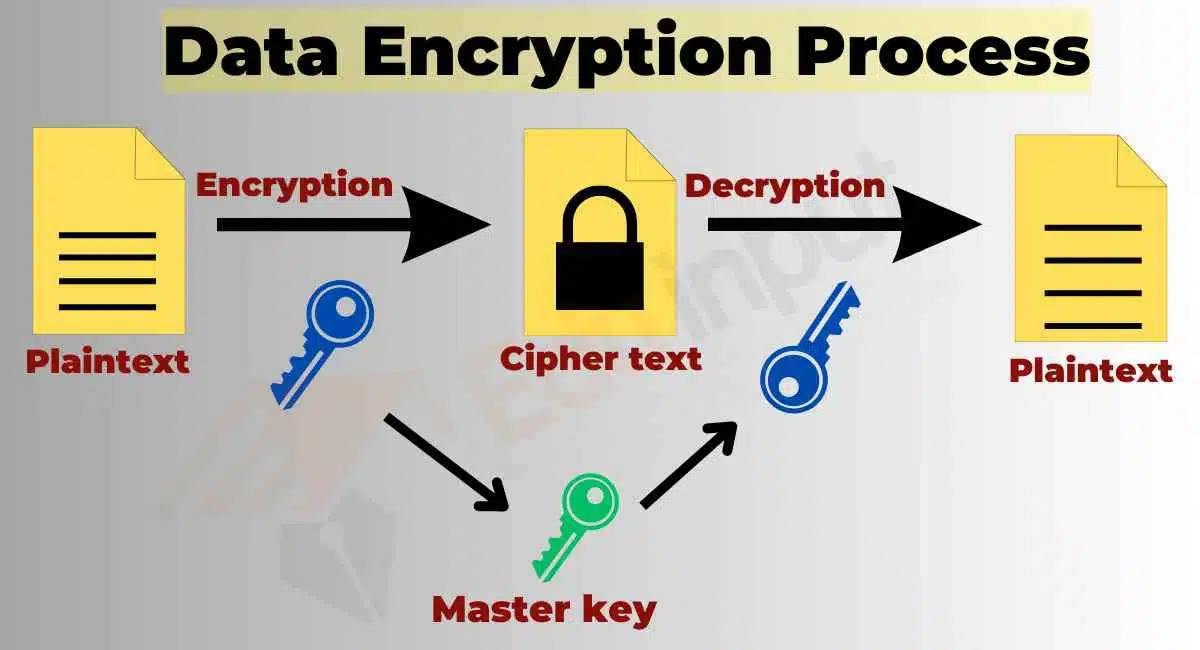
Encryption
Encryption is the process of converting data into a coded language to protect it from unauthorized access. Encryption can be used to secure data at rest, such as stored files and databases, or data in transit, such as emails and other network traffic.
Encryption can also be used to protect sensitive data, such as credit card information, medical records, and other personal information, from cyber threats.
Email Security
Email is a common vector for cyber-attacks, including phishing, malware distribution, and other types of cyber threats. Email security solutions can be used to protect against these threats, using methods such as spam filtering, antivirus scanning, and content filtering.
Email security can help prevent sensitive data from being compromised, reducing the risk of data breaches and other cyber-attacks.
Network security is essential for protecting computer networks and the data they contain from cyber threats. By implementing various types of network security protections, organizations can reduce the risk of cyber-attacks and protect their valuable assets.
Benefits of Network Security
Network security is essential for protecting computer networks and the data they contain from cyber threats. Here are some of the benefits of implementing network security measures:
Protects Against Cyber Threats
The primary benefit of network security is that it protects against cyber threats, such as viruses, malware, and hacking attempts.
Without proper network security measures in place, cybercriminals can gain access to sensitive data and cause significant harm to an organization.
Ensures Business Continuity
Network security helps ensure business continuity by preventing cyber-attacks that can disrupt operations. When a network is compromised, it can cause downtime, loss of productivity, and damage to an organization’s reputation. By implementing network security measures, businesses can avoid these risks and ensure that their operations remain uninterrupted.
Protects Sensitive Information
Network security measures protect sensitive information, such as financial records, trade secrets, and personal data. When sensitive information falls into the wrong hands, it can lead to financial losses, legal liabilities, and damage to an organization’s reputation.
Network security measures, such as encryption and access controls, can help prevent these risks and protect sensitive information from being compromised.
Helps Meet Regulatory Requirements
Many industries are subject to regulatory requirements that mandate specific network security measures to protect sensitive data. For example, healthcare organizations must comply with HIPAA regulations, which require the implementation of network security measures to protect patient data.
By implementing network security measures, businesses can ensure compliance with regulatory requirements and avoid potential penalties for non-compliance.
Improves Network Performance
Network security measures can also improve network performance by reducing the amount of network traffic and optimizing network resources.
For example, firewalls can block unnecessary network traffic, reducing network congestion and improving performance. Intrusion detection and prevention systems can also help identify and eliminate malicious traffic that can slow down network performance.
Reduces Costs
While implementing network security measures may require an initial investment, it can ultimately save businesses money by reducing the risk of cyber-attacks and other security incidents.
Cyber-attacks can result in costly downtime, data loss, and legal liabilities. By investing in network security measures, businesses can avoid these risks and reduce their overall costs associated with cyber threats.
Related FAQs
What are the 3 elements of network security?
The three elements of network security are :
Confidentiality: Confidentiality refers to keeping data private and protected from unauthorized access.
Integrity: Integrity means ensuring that data is accurate and has not been tampered with.
Availability: Availability refers to making sure that data and network resources are accessible to authorized users when needed
What is risk in network security?
Risk in network security refers to the potential for harm or loss due to a security breach or vulnerability in the network. This harm could be in the form of data theft, system downtime, or financial loss, among other things.
What is the biggest threat to network security?
Risk in network security refers to the potential for harm or loss due to a security breach or vulnerability in the network. This harm could be in the form of data theft, system downtime, or financial loss, among other things.
What is the biggest threat to network security?
The biggest threat to network security is often considered to be human error or negligence. This can include things like weak passwords, unsecured devices, and phishing scams. Other threats include malware, hacking attempts, and denial-of-service attacks.




Leave a Reply