Watch a video lecture on data communication and components of data communication.
Search Results for: data communication
Data Communication – Types, Components, Signals, and Encoding of Data
Data communication is the exchange of data between two devices via some form of transmission media such as a wire cable.
In other words, we can say that the transfer of information from one location to another is called data communication. The data can be transferred through the medium.
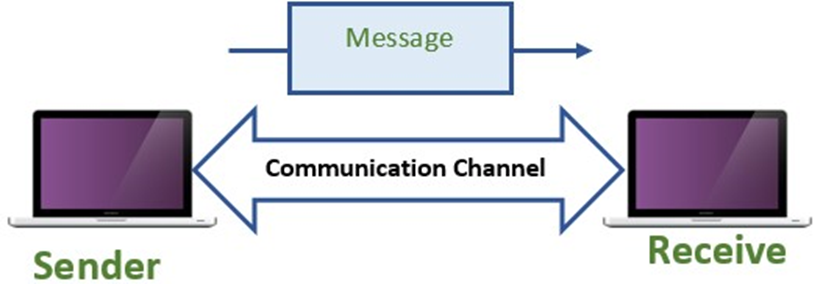
Key Points
| 1. Data communication is the exchange of data between two devices via transmission media. 2. The five components of data communication are message, sender, receiver, communication channels, and encoding/decoding. 3. Data can be represented as text, numeric data, images, audio, or video. 4. Computers represent data as binary numbers, with 0 representing no electrical pulse and 1 representing a pulse. 5. Encoding is the process of converting data into binary form. Types of coding schemes include BCD, EBCDIC, ASCII, Unicode, and others. |
Components of Data Communication
The five necessary models of data communication are as follows. Data communication is not possible without these components.
Message
The message is the data or information to be communicated.
It may consist of text, picture, audio, number, video, or any combination of these.
Sender
The sender is the device that sends the message. It is also called a source or transmitter.
It can be a computer, workstation, telephone, video camera, etc.
Receiver
The receiver is the device that receives the data. It is also called a sink.
It can be a computer, workstation, telephone, video camera, etc.
Communication Channels
The communication channel is the path that connects the sender and the receiver.
It is used to transmit data. The transmission media can be a physical cable or a wireless medium. it is also called the medium.
Encode and Decode
The encoder converts the digital signals to a form that can pass through a transmission medium (analog signal) and the decoder again converts the signal from the encoded form into digital form, which is understandable for the receiver.
Without them, two devices may be connected but not communicating, such as a student speaking Urdu who cannot understand a student who speaks only German without a translator.
Signals
The electromagnetic or light waves representing data are called signals.
These are used to transfer data from one device to another through a communication medium. Data communication signals can be in analog or digital forms.
Types of Signals
There are two types of signals for data communication
- Analog Signal
- Digital Signal
Analog Signals
An Analog signal is a continuous electrical signal in the form of a wave. This wave is known as a carrier wave. The telephone line is used media for the analog transmission of data. Sound, Radio, and microwave are also examples of analog signals.
Characteristics of Analog Signals
Frequency: The number of times a wave repeats during a specific time interval is known as frequency.
Amplitude: The height of a wave within a given period is known as amplitude.

Digital Signals
A Digital signal is a sequence of voltage represented in the binary form. The digital signals are in the form of electrical pulses of ON and OFF.
These signals are in discrete form. Most computers are digital and represent data as patterns of binary numbers. Digital signals are faster and more efficient.
Digital signal processing is used in many areas such as telecommunications, audio, speech, image, sonar, geophysics, and radar. In telecommunications, it’s used for digital transmission and switching. The text also talks about how radar signal processing works and gives examples of digital radar processing systems.[1]
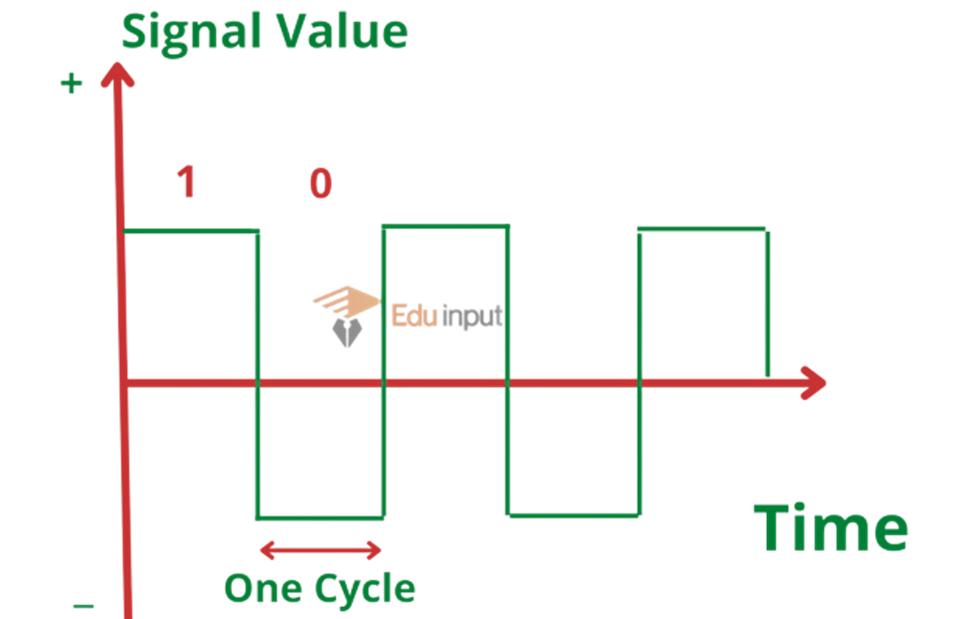
Types of Data
Data can be represented in different ways in data communication
Text Data
The text includes words, sentences, and paragraphs. Text processing refers to the ability to manipulate words, lines, and pages. Text is normally stored as ASCII code without formatting. e.g. Usama Khalil, Pakistan etc.
Numeric Data
Numeric data consists of digits from 0 to 9. It may also contain( +, -, .) Signs. It can be integer type or real type data.
Image
This type of data includes charts, pictures, graphs, and freehand drawings. The information in this form is more comprehensive.
The data are sent as contiguous bits, which for transfer, are packed into the 8- bit transfer byte. The receiving site must store data as contiguous bits.
Audio
Sound is the representation of audio. It is converted into digital code by sampling the sound waves 44,056 times per second and converting each sample into a 6-bit number. The audio data can be speech, music, or any type of sound.
Video
The video is produced either as a contiguous entity (by a camera) or it can be a combination of images, each a discrete entity, arranged to convey the idea of motion. Video is used to display a movement or action.
How is data represented on computers?
The computer works with binary numbers. The binary number maybe 0 or 1. The data inside the computer is represented as electrical pulses.
The binary digit 1 indicates the presence of an electrical pulse. The binary digit 0 indicates the absence of an electrical pulse.
The binary digit is known as a bit. It is an abbreviation of a binary digit. It is the smallest unit of memory. A collection of four bits is called a nibble. A collection of eight bits is called a byte. One byte can store a single character.
What is meant by the encoding Data?
The computer works with binary digits only. Therefore, numeric or non-numeric data must be converted into binary numbers before the computer can understand it.
The process of converting data into a binary form is known as encoding. Data can be converted into binary form by using different coding schemes.
Types of Coding Schemes
A coding scheme for communications is a binary system that is used in computer systems. The system consists of groups of bits (o and 1) that represent a character.
Some codes use different numbers of bits such as 5, 7, 8, and 9 to represent that during data communication. The following are some coding schemes to represent data.
BCD Code
BCD stands for Binary Coded Decimal. It is 4 bits of code. It means that each decimal digit is represented by 4 binary digits. It was used by early computers.
EBCDIC Code
EBCDIC stands for Extended Binary Coded Decimal Interchange Code. It is an 8-bit code primarily used by International Business Machines (IBM). It is normally used in mainframe computers. It can represent 256 characters.
ASCII stands for American Standard Code for Information Interchange. It is a 7-bit code and makes 128 character combinations, whereas an 8-bit can make 256 combinations.
ASCII Code
It was developed by American National Standards Institute (ANSI). It is the most widely used coding scheme for personal computers. The extended 128 unique codes represent graphic symbols.
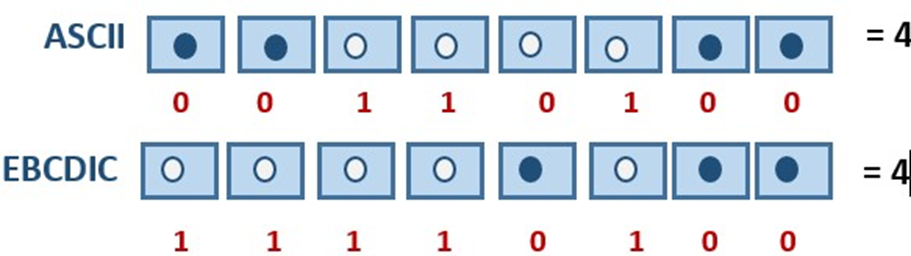
Unicode
Universal Code is a 16-bit code and can represent up to 65,536 symbols. Unicode has started to replace ASCII at all levels.
It supports a comprehensive set of mathematical and technical symbols to simplify scientific information With the UTF-8 (Unicode Transformation Format 8) encoding. Unicode can be used in a convenient and backward-compatible way in environments that were designed entirely around ASCII.
Related FAQs
Why is data communication important?
Data communication permits businesses to save money and function better by exchanging data and using the same equipment for multiple computers. The network can be set up through cables, phone lines, or infrared beams – which is more affordable and cuts back on expenses.
What are the 5 basic components of data communication?
The 5 basic components of data communication are:
· Sender
· Receiver
· Medium (communication channels)
· Message
· Set of rules (Protocol)
What is the signal?
Signals are electromagnetic or light waves that represent data.
What are the types of signals in data communication?
There are 2 types of signals in data communication:
Digital signal
Analog signal
What are data and types of data?
Data is the collection of raw facts and figures.
There are different types of data:
· Integer
· Text Data
· Numeric Data
· Audio
· Image
· Video
What is the use of data communication?
Data communication is the process of sending and receiving digital data between devices that are connected through a communication medium.
Data can be exchanged between devices like PCs, laptops, mobile phones, etc. that are connected through a network or other communication medium.
What is encoding in data communication?
Encoding is the process of translating data into a format that can be read and understood by a computer. Decoding is the reverse process of encoding, which is to convert encoded data back into its original format.
Does Switching Off Phone Data and WiFi Protect Me From Radiation From My Phone?
Switching off your phone’s data and WiFi does not protect you from radiation emitted by the phone itself. The radiation emitted by phones is primarily due to the radiofrequency energy used for communication, and this does not change whether data and WiFi are on or off.

To minimize exposure to phone radiation, use your phone less often, keep it away from your body when not in use, and consider using a radiation-reducing case.
Different Types of Phone Radiation
Smartphones emit two types of non-ionizing radiation:
Extremely low-frequency (ELF) radiation
RF radiation is produced when you make calls, use data, or connect to WiFi. ELF radiation is generated by the device’s internal components and power supply.
The Role of Data and WiFi
Data and WiFi connections contribute to your phone’s RF radiation exposure. When you use data or connect to WiFi, your phone constantly communicates with cell towers and routers, emitting RF radiation in the process. While these emissions are considered low, some individuals are concerned about prolonged exposure.
Does Switching Off Data and WiFi Help?
Switching off phone data and WiFi can indeed reduce your exposure to RF radiation, but the impact may be limited. When these features are turned off, your phone stops communicating with cell towers and routers, significantly decreasing RF radiation emissions. However, your phone will still emit ELF radiation from its internal components.
While switching off data and WiFi can lower your RF radiation exposure, there are other factors to keep in mind. Phone radiation levels vary depending on factors like signal strength, distance from cell towers, and the duration of usage. Additionally, using wired headphones instead of holding the phone to your ear can also decrease radiation exposure.
Tips for Reducing Phone Radiation Exposure
- Use Speakerphone: Switching to speakerphone mode keeps the phone away from your head, reducing radiation exposure to your brain.
- Texting: Communicating through text messages reduces the time your phone is held close to your body.
- Airplane Mode: Activating airplane mode disables all wireless connections, minimizing radiation emissions.
- Limit Lengthy Calls: Prolonged phone calls increase exposure time; keep calls short when possible.
Practical Steps for Minimizing Risk
- Keep Phone Away While Sleeping: Place your phone away from your bed to minimize nighttime exposure.
- Use Wired Accessories: Wired headphones and accessories reduce the need to hold the phone close to your body.
- Stay Informed: Stay updated on research about phone radiation and make informed choices based on credible sources.
Difference between Computer Science and Data Science
The key difference between computer science and data science is, computer science is the study of the design, architecture, and maintenance of computer systems, software, and its applications.
While data science is the study of data that deals with a large amount of data by using different data visualization techniques.
Computer Science and Data Science are related but distinct fields. In this article, we will discuss the main differences between data science and computer science which will be helpful for you to find the difference between both of them.
What is computer science?
Computer science is the study that deals with the design, development, and maintenance of computer systems, software, and applications. It involves the principles of programming languages, algorithms, software engineering, computer architecture, operating systems, databases, computer networks, and artificial intelligence.
Computer scientists use many technologies to solve complex problems and prepare for the future. They also write programs that create different applications. Their main focus is validating models of human-computer interaction with people or machines to develop efficiencies where needed.
What is Data science?
Data science is the study that involves the use of statistical and computational techniques to extract insights and knowledge from data. It combines computer science, statistics, mathematics, and domain expertise to analyze large and complex data sets and inform decision-making.
Data Science requires a strong knowledge of computer science, mathematics, and statistics, as well as the ability to work with large and complex data sets. The data scientist has strong communication skills to communicate with stockholders for better understanding.
Computer science vs Data Science
The main differences between computer science and data science are given below:
| Computer science | Data Science |
| Architecture and design are studied in computer science. | In data science, data is manipulated and analyzed. |
| Speed and Performance | Reduction in Data Redundancy |
| Computer science is less valuable than data science. | Data science is more valuable than computer science. |
| It exists for many years. | It is a recently developed branch of technology. |
| We earn less in computer science as compared to data science. | We can earn more in data science as compared to computer science. |
| It is used in: Computers Networks Software engineering Security Databases Programming languages Informatics Algorithm designing Bioinformatics | It is used in: Big data analytics User-behavior analysis Data Engineering Fraud detection Recommendation Machine learning Customer analytics Operational analytics Predictive analytics, etc. |
| Computer science is used for Game development Web development database management IT consultant, etc. | Data science is used for Data modeling Data analysis Data architecture, etc. |
Uses of Computers in Communication
One of the most important uses of computers is communication. The computer has made the world a global village. That everyone is connected with each other. It is also playing a significant role in the defense departments, agriculture, education, the field of chemistry, For office automation, at home, and the market, etc.
In past, people travel a lot of distances even distances of months to meet their relatives but now computers provide the facility of communication within seconds. We can connect with our relatives with just a single call.
Some Uses of computers in communication are given below:
Sending and receiving emails
The computer is very useful for sending electronic mail. It also receives emails. Most offices, banks, and hospitals use computers to send emails.
Computer conferencing
The computer is helpful for conference calls. This is mostly used by businessmen or heads of offices use for conference calls in which all the members connected with each other through calls and share their ideas.
Most deals are done through computer conferencing. In the modern era, it is very useful for people who start an online business because all their meetings are through computer conferencing.
Example
Video conferencing allows people sitting in different parts of the world to participate in a conference. It is mostly used in businesses.
Post news
The computer is also used for viewing and posting the news. Basically, this is also the type of communication because in this way everyone gets information about others and now what’s happening around them.
Example
Actors posts about their life on the internet and in this way their fans stay tuned and connected with their life. With much more advantages the internet has some disadvantages.
Video calls
Now people can see each other through video calls. People are only a short distance away from each other. It permits people to meet at a common time over long distances. Video calls save time and also keep the cost of traveling.
Example
In the past people have no source of communication rather they have to go to that place to meet their relatives but now computers provide them with this facility that they can communicate with each other through computers.
Bulletin board system
This system also helps in communication. This software allows the bulletin board system to answer the calls that are received from the user’s computer and it also stores messages and allows access to the information stored in its files. Users can also take part in ongoing discussions or share their ideas.
Example
Bulletin is provided for such people who have the same interests. It is provided for a group of employees, patients, students, and teachers.
Satellite communication
This system is used for the telecommunication of radio and television signals. Channels are employed for the transfer of a large amount of data. Satellite transmission media is the fastest way of sending voice, texts, videos,s or images over long distances.
Social Media Communication
The computer also provides the facility for social media communication. Social media is based on online communication channels in which. the group-based input can be done through social networking or communication. Social media helps to share the views of the public.
Frequently Asked Questions (FAQs)
How do you use the computer for communication?
One of the most important uses of computers is the ability to communicate with others. In a way, you could say that computers have made the world feel smaller by connecting people from all corners of the globe. Through the use of computers and various forms of technology, people from different parts of the world can communicate with each other easily and effectively.
What is the common tool for communication?
External and internal communication requires the use of a variety of tools such as mail, email, telephones, cell phones, smartphones, computers, video and web conferencing tools, social networking, as well as online collaboration and productivity platforms.
What type of communication happens on computers?
Simplex type communication occurs in computer networks when information only travels in one direction. This type of communication is often used for point-to-point connections, like those between a computer and a printer.
Data Dictionary in DBMS–Types of Data Dictionary
Data Dictionary is a repository of information that describes the logical structure of the database. It contains record types, data item types, data aggregates, etc. Data dictionaries in some systems store database schema and can be used to create and process databases. The data dictionary contains metadata. Metadata is the data about the data stored in the database.
Uses of Data Dictionary
Different uses of the data dictionary are as follows:
Information about data
A data warehouse is a type of database that is used to collect and store information from multiple sources in one central location. This helps management get control over data and use it as a resource more effectively.
Communication with user
Data dictionaries provide great help when it comes to communication, as they store the precise meanings of data items. It is crucial that an exact definition of each item is stored in the data dictionary, as this can be used in case of any problems.
Record of change in database structure
The data dictionary is like a history book for your database. It keeps track of changes to the database structure, such as the creation of new data items or modification of data item descriptions. This way, you can refer back to the data dictionary to see how the database has changed over time.
Determining the impact of change
A data dictionary is like a map that shows all of the items in a database and how they are related to each other. This is important for database administrators (DBAs) because it can help them see the potential effects of a change before they make it.
Recording Access control information
The data dictionary is a crucial part of any organization’s security infrastructure. It stores information about who is authorized to access what data, and it also defines the types of access each user has. By keeping this information up-to-date and accurate, the data dictionary helps to ensure that only authorized users can access the data they need.
Audit information
It also keeps a record of each access to the database. This information can later be used for audit purposes.
Types of Data Dictionary in DBMS
Different types of data dictionaries are as follows:
Integrated Data Dictionary
A data dictionary that is part of DBMS is called an integrated data dictionary. It performs many functions throughout the life of the database not only in the design phase. There are two types of integrated data dictionary:
Active Data Dictionary
The integrated data dictionary is called active if it is checked by DBMS every time a database is accessed. It is always consistent with the actual database structure. It is automatically maintained by the system.
Passive Data Dictionary
The integrated data dictionary is called passive if it is not used in day-to-day database processing.
Freestanding Data Dictionary
A data dictionary that is available without a particular DBMS is called a freestanding data dictionary. It can be a commercial product or a simple file developed by the designer. Many CASE packages provide a data dictionary tool. It is preferable in the initial design stages before choosing any particular DBMS
Distributed Database Management System (DDBMS)–Advantages and Disadvantages
Users access the distributed database through a variety of applications, each designed to provide a specific set of functionality. In a distributed database system database, the applications running at any of the system’s sites should be able to operate on any of the database fragments. The software that is used to manage a distributed database is called a “distributed database management system” (DDBMS).
DDBMS Motivation
Many organizations are naturally distributed over different locations. For example, a company may have locations in different cities, or a bank may have multiple branches. It is natural for databases used in those organizations to be distributed over these locations. An important requirement of such a distribution is that the users can access data both locally and at other locations.
Advantages
Different advantages of distributed databases are as follows:
Local Control
Local data is owned and managed locally. Security, integrity, storage representation, and hardware are controlled locally. However, users can access remote data when necessary.
Reliability and Availability
When a centralized system fails, the database is unavailable to all users. A distributed system will continue to function at some reduced level when a component fails. It continues to operate if one or more sites go down or communication links fail.
Efficient Querying Processing
Queries about data stored locally are answered faster. The queries can be split to execute in parallel at different sites or they can be redirected to less busy sites.
Modular Growth
It is much easier to add another site to the distributed system than to expand a centralized system. Suppose that an organization expands to a new location or adds a new workgroup. It is often easier and more economical to add a local computer and its associated data to the distributed network than to expand a large central computer.
Economic
It costs much less to create and maintain a system of smaller computers with the equivalent power of a single large computer.
Disadvantages
Some disadvantages of the distributed database system are as follows:
Software Complexity & High Costs
A DDBMS is more complex than a centralized DBMS. Therefore, it is more expensive to buy and maintain. There are also additional manpower costs to manage and maintain the local DBMSs and the underlying network.
Processing Overheads
The various sites must exchange messages and perform additional calculations to ensure proper coordination among data at the different sites.
Data Integrity
It is harder to enforce data integrity when data is updated at different sites simultaneously.
Complex Database Design
Besides the normal difficulties of designing a centralized database, the design of a distributed database has to take account of fragmentation and replication of data, and allocation of fragments.
Slow Response
If the data are not distributed properly according to their usage, or if queries are not formulated correctly, response to requests for data can be extremely slow.
Functions of a DDBMS
A distributed DBMS provides access to data at various sites. A DDBMS is required to perform the following functions in addition to the functions of a DBMS:
• Extended communication services to provide access to remote sites and allow the transfer of queries and data among them.
• Extended system catalog (Global System Catalog) to store data distribution details; this way can determine the location from which to retrieve requested data.
• Distributed query processing. If necessary, translate the request at one site using a local DBMS into the proper request to another site using a different DBMS and data model.
• Extended concurrency control to maintain consistency of replicated data.
• Extended recovery services to be able to recover from individual site crashes and failure of communication links.
Data Transmission Modes–Types of Data Transmission
The way to transmit data from one device to another must be connected via a cable or wire. The connection is called a link. There are two types of links: wired (cable) and wireless (radio).
Types of data Transmission Modes
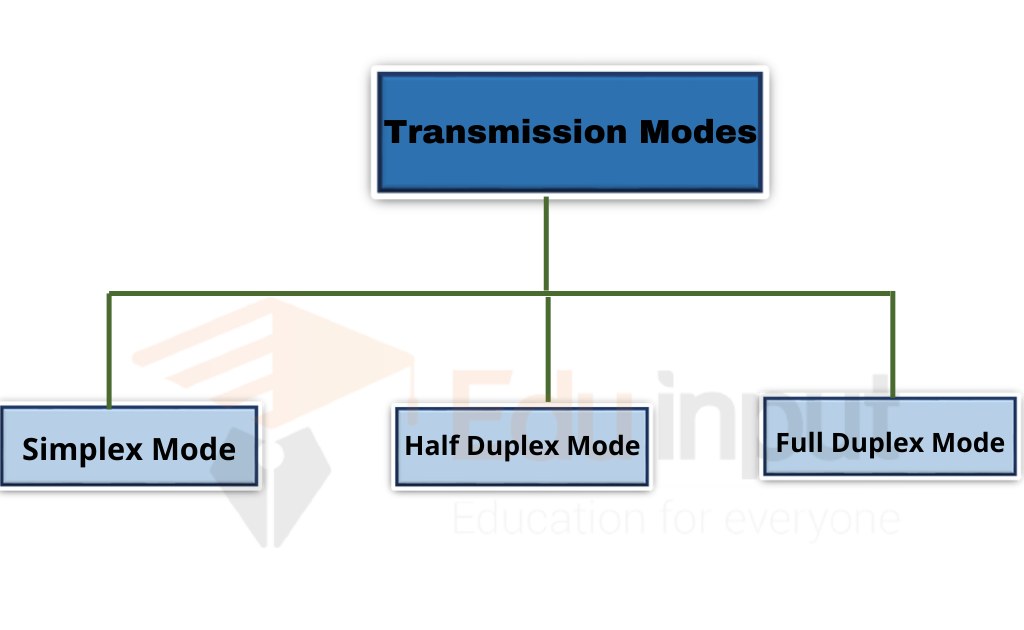
There are three types of data transmission modes
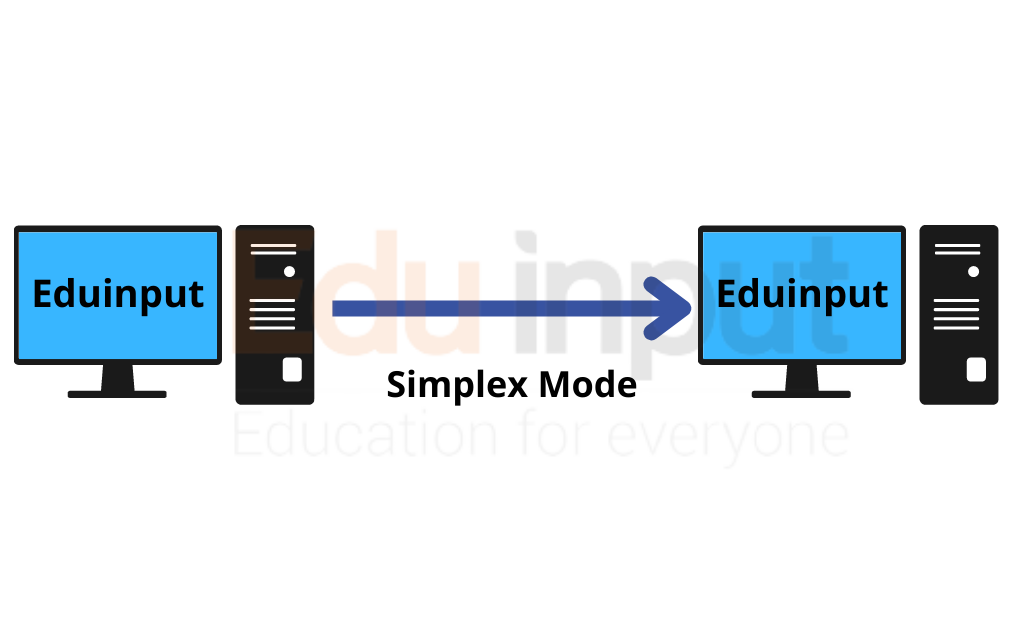
Simplex Transmission Mode
Simplex transmission mode (STM) is a method of data communication between two or more devices or computers over a single wire pair. This method is commonly used in telephone systems, cable television networks, and some wireless networks. In STM, each device transmits at the same time, and only one device receives it at a time.
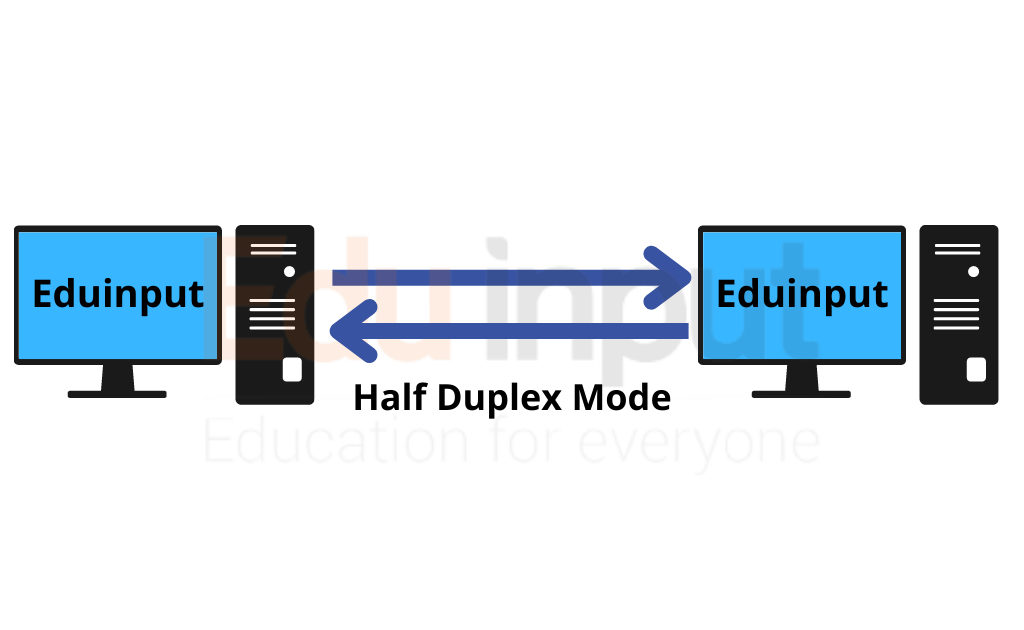
Half Duplex Mode
Half duplex mode means that only one side of the communication line can transmit data at a time. For example, if you want to send a message from your PC to another device such as a printer or scanner, you would connect both devices to the same network cable using a switch (or hub).
The switch then connects each device to the other via two separate cables. Half duplex mode allows you to communicate between the two devices simultaneously.
You can use half-duplex mode to transfer files between computers. This method is useful when transferring large amounts of data over long distances. In addition, you can also use half-duplex mode when sending email messages.
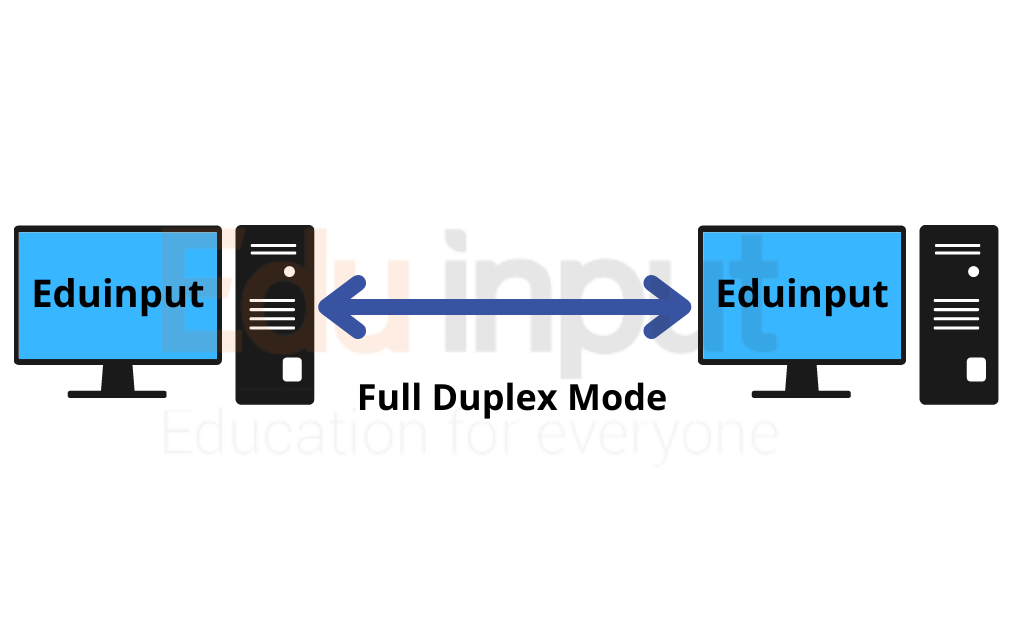
Full Duplex Mode
“A full-duplex communications system is a communications system capable of simultaneous transmission and reception.”
Full Duplex Transmission Mode (FDT) is a method of communication between two devices where both parties send data at the same time. The main difference between FDT and Half Duplex Transmission Mode (HDT) is that HDT allows only one party to transmit at a given time. This means that the other party cannot hear or respond to the message until the sender has finished transmitting.
Types of Data Transmission
There are two types of data transmission
Serial Transmission
Serial data transmission is the simplest type of data transfer between two devices. In serial data transmission, each bit of information is sent over a single wire at a time. A device sends out a series of 1’s and 0’s, called bits until the entire message is transmitted.
Each bit is represented by a voltage level on the wire. When a 1 is sent, the signal goes high; when a 0 is sent, the signal stays low.
Parallel Transmission
Parallel transmission refers to a method of transmitting data over multiple wires at once. This technique allows for faster transfer speeds compared to serial transmission.
Frequently Asked Questions (FAQs)
What are the three transmission modes?
Simplex Mode
Half-duplex Mode
Full Duplex Mode
What is the data transmission mode?
Data Transmission Mode (DTM), also known as DTCM, is a method of transmitting data over a radio frequency band using amplitude modulation.
What is the parallel transmission?
Parallel transmission defines a transmission structure that shares multiple data bits at a similar time over separate media. In general, parallel transmission can be used with a wired channel that uses multiple, separate wires.
What is an example of serial transmission?
Examples of serial mode transmissions include connections between a computer (e.g., a personal computer) and a modem using the serial port interface.
Optical Fiber Communication-Applications And Advantages
Optical Fiber Communication is the type of communication in which signals are transmitted in form of light. The Fiber optics principle for the propagation of light is total internal reflection. there are many types of optical fiber but there are so some power losses in optical fiber during communication
Optical Fiber Communication
A fiber optic communication system consists of three major components.
- Transmitter
- Optical fiber
- Receiver

Transmitter:
It converts electrical signals to light signals.
Optical fiber:
It is used for guiding the signals.
Receiver:
It captures the light signals from the fiber and converts them into electrical signals.
Working of a transmitter in optical fiber communication
The light source in the transmitter can be either a semiconductor laser or a light emitting diode (LED). In these devices light emitted is an invisible infra-red signal. The typical wavelength is 1.3 µm. Such light will travel much faster through optical fibers than will either visible or ultra-violet light.
The lasers and LEDs used in this application are tiny units in order to match the size of the fibers which is less than half the size of the thumbnail.
Modulation in optical fiber communication:
Modulation is necessary for the light waves to transmit information by light waves, whether it is an audio signal, a television signal, or a computer data signal.
The most common method of modulation is called digital modulation in which the laser or LED is flashed on and off at an extremely fast rate. A pulse of light represents the number ‘1’ and the absence of light represents zero.
Working of optical fiber:
In a sense, instead of flashes of light traveling down the fiber ones (1s) and zeros (0s) are moving down the path.
Working of the receiver:
With computer-type equipment, any communication can be represented by a particular pattern or code of these 1s and 0s. At the end of the fiber, a photodiode converts the signals which are then amplified and decoded.
The receivers are programmed to decode the 1s and 0s it receives the data in the form of sound pictures or data as required. Digital modulation is expressed in bits (binary digit) or megabits (106 bits) per second where a bit is a 1 or a 0.
Repeaters:
Even though the ultra purity tees 99.99% glass of the optical fiber, the light Signals eventually become dim and are regenerated by devices called repeaters. Repeaters are typically placed about 30km apart, but in the newer systems, they may be separated by as much as 100km.
Applications of Optical Fiber communication
Optical fiber communication is used in many fields, In the medical, it is used as light guides, imaging tools, and also as lasers for surgeries. Some other applications are
- Data Storage
- Defense/Government
- Networking
- Telecommunications
- Broadcast
- Community antenna television
Advantages of Optical fiber communication
There are many advantages of using Optical fiber communication. It gives better bandwidth. Fiber optic cables have much greater bandwidth than metal cables.
Higher bandwidth means the optical fiber has a faster speed. There are also many other advantages of using Optical fiber communication.
- Longer transmission distances
- Improved latency
- Greater flexibility
- Stronger security
Communication Channel | Types of Communication Channel
The path through which data transfers from one computer to another is communication media or communication channels.
The communication channel is the path that connects the sender and the receiver. It is used to transmit data. It can be a twisted–pair wire, coaxial cable, fiber optic cable, microwave, etc. it is also called the medium.
Data is sent from a source to a destination through a communication channel. The channel is defined by its bandwidth, attenuation, and propagation delay. The signal may lose quality as it travels through the channel, so it needs to be regenerated at certain points. The channel is established by transmission lines, including two-wire lines, co-axial cables, microwave radio, optical fibers, and satellites.[1]
Key Points
- Communication media is the path through which data transfers between computers.
- It can be a physical wire or wireless signal, connecting the sender and receiver.
- There are two types of communication channels: guided (physical wire) and unguided (wireless).
- Guided media includes twisted-pair, coaxial, and fiber optic cables.
- Twisted-pair is inexpensive but has lower bandwidth, coaxial is expensive but good for long distances, and fiber optic uses light pulses for high speed and low interference.
- Unguided media includes microwaves, communication satellites, and mobile communication.
- A microwave uses radio waves for high-speed transmission but requires line-of-sight.
- Communication satellites receive and retransmit signals from earth stations and can handle large volumes of data, but are vulnerable to interference from bad weather.
Types of Communication Channel
There are two types of communication channel
Guided Media
The physical path to transmit data is called guided media. In guided media, a physical wire is required to connect the devices. It is also known as bounded media.
There are different types of guided media
Twisted pair cable
It is the most commonly used communication medium. It is made up of copper. In twisted pair, two wires are twisted to reduce the noise. Noise is an electrical disturbance that can degrade the communication. It is normally used in local telephone communication.
It is used for short-distance digital data communication. It is also called wire pair. Its speed is 9600 bits per second at a distance of 100 meters. Wire pairs are inexpensive. It has less bandwidth than coaxial cable or fiber optics.
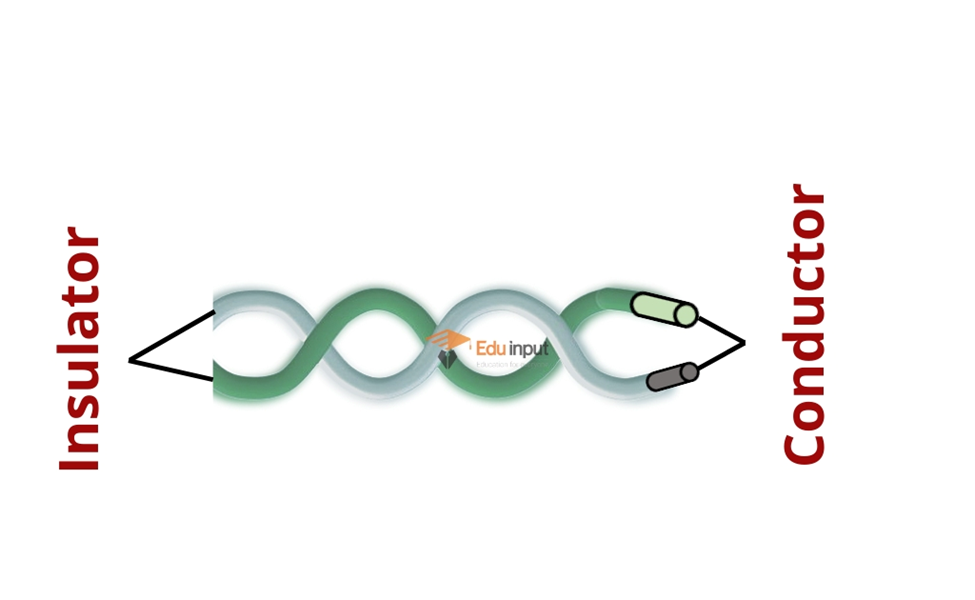
Coaxial Cable
Coaxial cable consists of a copper wire core covered by insulating material. The insulated copper wire is shielded by copper mesh. It secures the cable from electromagnetic waves. It is the same cable that is used for television. Coaxial cables contain 4 to 22 coaxial units called tubes.
It is used for long-distance telephone lines and local area networks. It is more expensive than twisted pair.
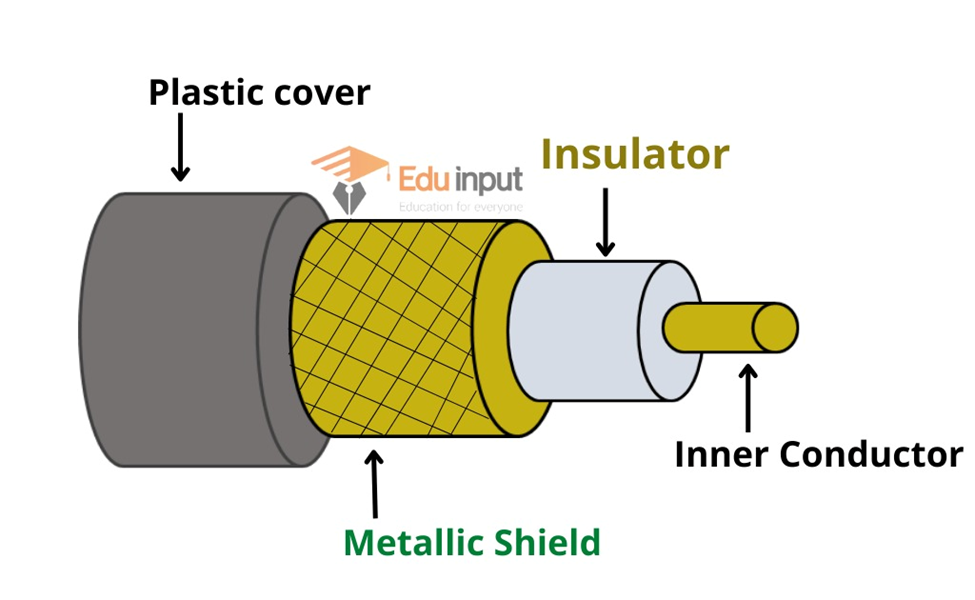
Fiber Optics Cable
Fiber optic cable transmits data through tiny tubes as pulses of light. A typical fiber optic consists of a very narrow strand of glass known as a core. The strands are very thin like human hair. The core is the center of the fiber from where light travels.
There is a concentric layer of glass around the core known as cladding. It reflects the light into the core. The cladding is protected with a coating of plastic called a jacket.
The important characteristic of fiber optics is refraction. ISI and cable TV use fiber optic in their network.

Unguided Media
There are different types of unguided media that are used in communication
Microwave
Microwaves are radio waves that provide high-speed transmission. Voice and data can both be transmitted through microwaves. Data is transmitted through the air from one microwave station to another similar to a radio signal.
line-of-sight transmission is used in microwaves. It means that the signals travel in a straight path and cannot bend. Microwave stations or antennas are usually installed on tall towers or buildings. Microwave stations are placed within 20 to 30 miles of each other.
Each station receives the signal from the previous station and transfers it to the next station. Data is transferred from one place to another in this process. There should be no buildings or mountains between microwave stations.
Communication Satellite
A communication satellite is a space station. It receives microwave signals from the Earth station. It amplifies the signals and retransmits them back to Earth. A communication satellite is established in space about 22,300 miles above the earth.
The data transfer speed of communication satellites is very high. The transmission from earth station to the satellite is called uplink. The transmission from the satellite to earth station is called the downlink.
An important advantage of the satellite is that a large volume of data can be communicated at once. The disadvantage is that stormy weather can severely affect the quality of satellite transmission
Mobile Communication
Mobile communication is a radio-based network. It transmits data to and from a mobile computer. In mobile communication, the computer can connect to the network through wired ports or wireless connections.
Related FAQs
what is a communication channel?
Communication media or communication channels refer to the route through which data is transferred from one computer to another.
Write different types of communication channels.
The communication channel has two types:
1. guided media
2. Unguided media
Write different types of guided media.
Twisted Pair Cable
Coaxial Cable
Fiber Optic Cable
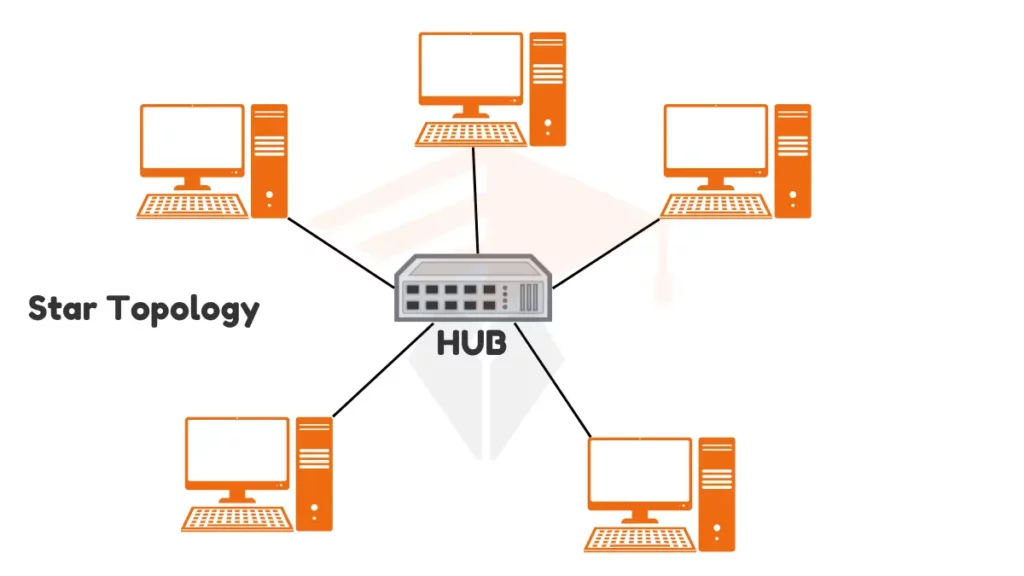
What is Star Topology -Types, Components and Working
Star topology is a computer network configuration where all devices connect to a central point. This central point can be a hub or a switch. The devices connected to the hub are called peripheral nodes.
Each peripheral node has its dedicated connection to the hub. The network’s layout resembles a star, with lines (cables) extending from the central hub to each device. This structure helps keep the network organized and easy to manage.
Types of Star Topology
Star topology can be divided into two main types:
1. Passive Star Topology:
In passive star topology, the hub does not process data. It simply acts as a connection point for devices. This type is cheaper and easier to set up. But may not perform as well in large networks. Passive hubs do not amplify or regenerate signals, which means that signal strength may weaken over long distances
2. Active Star Topology:
In active star topology, the central hub has its power supply and can process data. This hub type is more powerful and can manage more significant amounts of data. It improves network performance by allowing the hub to handle data traffic efficiently. Active hubs can also regenerate signals, which helps maintain strong connections over longer distances.
Components of Star Topology
the following are the components of star topology
1. Peripheral Nodes:
Peripheral nodes are the devices connected to the hub. These can include computers, printers, scanners, and other devices that need to connect to the network. Each device has a cable connecting it to the central hub. This individual connection allows each device to communicate directly with the hub, ensuring fast and reliable data transfer.
2. Central Node:
The central node, or hub, is the heart of the network. It acts as a control center for data communication. When one device wants to send data to another, it first sends that data to the hub. The hub then forwards the data to the appropriate device. The central hub helps manage the flow of information and ensures that data is sent to the right place. It can be a simple device with advanced features to improve network performance.
How Star Topology Works?
In star topology, when a device wants to send data to another device, it sends it to the hub first. The hub then processes this data and sends it to the correct destination, helping ensure that data travels quickly and efficiently.
Star topology also helps reduce data collisions. A data collision occurs when two devices try to send data at the same time. In a star network, all data passes through the central hub, which helps coordinate the communication. The hub manages the data flow, so it is easier to avoid collisions and keep the network running smoothly. This feature is essential in busy networks where many devices are communicating at the same time.
Examples of Star Topology
Let’s look at an example to understand this better:
Real-world Applications
Star topology is commonly used in various settings. For example, many schools use it to connect computers in a lab, allowing students to access shared resources like printers and files easily. Offices often use star topology to connect computers and printers, enabling employees to work together efficiently. Hospitals also use this setup to connect medical devices and computers, allowing for quick communication and data sharing among healthcare professionals.
FAQs
What are the three importance of stars?
They emit light and energy, guiding navigation and timekeeping
What is the purpose of a star?
The purpose of a star is to:
Emit light, Produce energy, Guide Navigation
What are the main advantages of a star network?
Easy setup, Good performance, Simple troubleshooting, Reliable
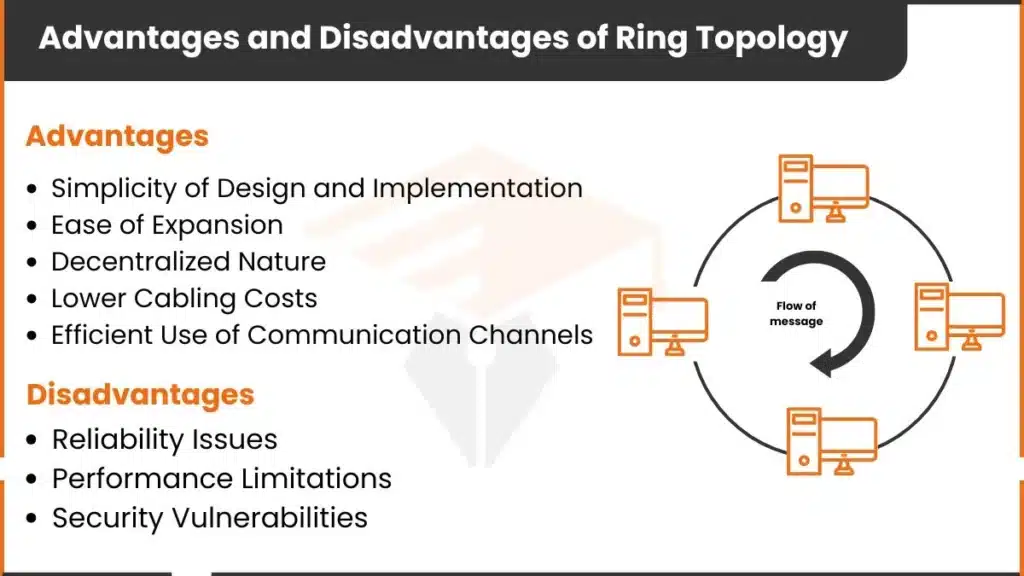
Advantages and Disadvantages of Ring Topology
One main advantage of ring topology is its simple setup and cost-effectiveness. It requires less cabling than other network designs. However, it has some notable disadvantages as well. The primary drawback is its vulnerability to single points of failure. If one device goes down, it can disrupt the entire network.
Advantages of Ring Topology
The following are the benefits of ring topology
1. Simplicity of Design and Implementation
The design of ring topology is straightforward. Each device connects to its neighboring devices on either side. This structure is easy to understand and set up, making it useful for beginners.
Because of this simple design, network administrators can set up the network quickly. Each device is part of a clear path, and data flows in one direction. This simplicity can make ring topology a practical choice for small to medium-sized networks.
2. Ease of Expansion
Adding more devices to a ring topology network is simple. New devices can be inserted between two existing devices without major changes to the network. This ease of expansion makes ring topology flexible. If a network grows or new devices are added, the process remains manageable. There’s no need to redesign the entire setup, which can save time and effort.
3. Decentralized Nature
In a ring topology, there is no central device or hub. Each device plays an equal role in the network. This decentralized design means the network does not rely on a single device to control data flow. If one device stops working temporarily, it may slow down the network, but it won’t completely stop it. This feature is an advantage in settings where each device needs to have equal access to data.
4. Lower Cabling Costs Compared to Other Topologies
Compared to other setups, ring topology usually requires less cabling. In a star topology, each device needs a separate connection to a central hub. But in ring topology, each device only connects to two others. This reduces the cost of cables and installation. In smaller networks, the savings on cabling can make ring topology a more affordable option.
5. Efficient Use of Communication Channels
Data travels in a single direction in a ring topology. This clear, one-way path avoids confusion or interference. Each device passes data to the next in an organized sequence, making the use of channels efficient. Because there’s only one path for data to travel, there are fewer delays. This efficiency can make ring topology a good choice for networks that don’t need high-speed connections.
Disadvantages of Ring Topology
Here are some drawbacks of ring topology:
1 . Reliability Issues
- Single Point of Failure
If one device fails, the entire network can be disrupted. Each device is like a link in a chain. So if one link breaks, the whole chain is affected. When a device stops working, data cannot continue to the next device. This issue makes ring topology less reliable than some other types of networks. - Difficulty Isolating Problems
In a ring topology, finding the exact location of a problem can be difficult. Since each device is connected in a loop. An issue with one device affects all others. Technicians may need to check each connection to find the source of the problem. This process can take time and may require disconnecting multiple devices. For networks where quick troubleshooting is important, this difficulty can be a challenge.
2. Performance Limitations
- Bandwidth Constraints as More Nodes Are Added
The more devices that are added to a ring topology, the slower the network may become. Each device has to handle data from every other device in the loop. With each new device, there is more “traffic” in the network. This can create bandwidth constraints, which means the network’s capacity is limited. - Higher Latency Due to Data Passing Through Multiple Nodes
Data has to pass through multiple devices to reach its destination in a ring topology. This creates latency, which is a delay in data transmission. For each device the data passes through, there is a small delay. If the network is large, the total delay can become noticeable. This higher latency can be an issue for tasks that need fast data transfer like video streaming or gaming.
3. Security Vulnerabilities
- Easier to Intercept Data
Since data passes through every device, it can be easier to intercept. Each device has access to the data as it travels through the network. This makes it possible for someone to “listen in” on the data. In high-security networks, this openness can be a risk. Sensitive data might be exposed as it moves through each device. - Potential for Malicious Nodes to Disrupt the Network
If one device in the network is compromised by malware or a malicious program, it can disrupt the entire ring. A malicious device can block or change data as it moves through the network. This can cause problems for all other devices in the ring. For networks with high-security needs, this risk can be a serious disadvantage of ring topology.
FAQs
Is it a ring main series or parallel?
A ring main is a series connection, as devices are connected in a loop, one after another.
Are ring circuits safe?
Ring circuits can be safe if properly installed and maintained
Where is the ring system used?
The ring system is used in LANs for data communication, electrical circuits for power distribution, fiber optic networks for redundancy, and utility networks like water or gas systems for continuous flow.
Third Chapter Solved Exercise MCQs Of ICS First Year Computer Science
Third Chapter Solved Exercise MCQs of ICS First Year Computer Science offers a collection of multiple-choice questions with answers, tailored for FSC students. This resource helps students review key concepts, practice for exams, and improve their understanding of the second chapter in Computer Science.
Third chapter solved MCQs with explanation
1. Microwave transmission, coaxial cables, and fiber optics are examples of.
(a) Modems
(b) Communication links
(c) Getaways
(d) Ring network
Explanation: These are physical channels used to transmit data.
2. Data communication requires only a:
(a) Sender
(b) Receiver
(c) Transmission Medium
(d) All of the above
Explanation: Data communication involves a sender, receiver, and transmission medium.
3. BIT stands for
(a) Binary Integer
(b) Binary digit
(c) Binary interval.
(d) None of the above.
Explanation: A bit is the smallest unit of data in a computer.
4. Communication between a computer and a keyboard involves transmission.
(a) Simplex
(b) Half-duplex
(c) Full-duplex
(d) Automatic
Explanation: a one-way communication system where information is transmitted from one device to another, but the receiving device cannot send information back to the transmitting device.
5. The is the physical path over which a message travels.
(a) Protocol
(b) Medium
(c) Single
(d) All the above
Explanation: The physical path over which a message travels is called the medium.
11th Class Computer Science Book PDF download- chapter wise
Get into the world of computer science with our comprehensive 11th Class Computer Science PDF Book Punjab Board. Get Downloadable Chapter-Wise Books covering topics like Basics of Information Technology, Information Networks, Computer Architecture, and Fundamentals of the Internet. Perfect for students looking for Intermediate Part 1 Books PDF or Free Textbooks for Class 11 across All Subjects. Punjab Board 11th Class Textbooks are available in Urdu and English Medium on our platform.
Along with the PDFs, you get Free Study Material for Class 11, Chapter-wise Important Questions, and 11th Class Exam Preparation Resources to help you excel in your studies.
Chapter Wise FSC Part 1 Computer Science Book
click on the link to download the book:
Chapter 1 – Basics of Information Technology
Chapter 2 – Information Networks
Chapter 3 – Data Communications
Chapter 4 – Applications and Uses of Computers
Chapter 5 – Computer Architecture
Chapter 6 – Security Copyright and the Law
Chapter 7 – Windows Operating System
Chapter 9 – Spreadsheet Software
Chapter 10 – Fundamentals of Internet
Introduction To Computer Science-History, Scope, Branches and uses
Introduction Of Computer Science
Computer science involves the study of computation, automation, and information and spans theoretical disciplines to practical disciplines such as the design and implementation of hardware and software.

Computer science is an interdisciplinary branch of study. It combines ideas from mathematics, physics, biology, electrical engineering, and philosophy. It has been said that a computer scientist is someone who is capable of building a computer.
The traditional study of computer architecture, programming languages, and software development are some of the major subfields of computer science. Computational science, the use of algorithmic techniques for modeling scientific data, graphics and visualization, human-computer interaction, databases and information systems, networks, and the social and professional issues that are unique to the practice of computer science are included.
Some of these subfields are related to other modern fields such as bioinformatics and computational chemistry. A tendency among computer scientists to recognize and act upon their field’s many interdisciplinary connections is what leads to these overlaps.
History Of Computer Science
Although first proposed in 1956, the term “Computer Science” appears in a 1959 article in Communications of the ACM, in which Louis Fein argues for the creation of a Graduate School in Computer Sciences.
A large amount of computer science does not involve the study of computers at all. The term computing science has been used by some departments of major universities to emphasize that difference.
The term datalogy was suggested by a scientist to reflect the fact that the scientific discipline revolves around data and data treatment, while not necessarily involving computers.
The Department of Datalogy at the University of Copenhagen was the first scientific institution to use the term, with Peter Naur being the first professor in Datalogy. Most of the time, the term is used in Nordic countries. Data science is an alternative term proposed by Naur and is now used for a multi-disciplinary field of data analysis, including statistics and databases.
Father of Computer
Charles Babbage was a renowned mathematician in the 1800s who is considered by many to be the father of computing. This is largely due to his concept of the Analytical Engine in 1837, which was a machine that could be programmed to carry out complex calculations. It contained an ALU (arithmetic logic unit), basic flow control, and integrated memory – all hailed as major breakthroughs for computing at the time.
Unfortunately, Babbage was never able to fully fund the construction of his machine and it was only ever completed after his death by others who took interest in his work.
The word computing came into existence around 1910-1911. At that time a few people were working with mechanical computers. They were using devices like Jacquard Loom, etc. They were using them for calculating purposes. But they could not predict what would happen in future.
So they started calling these devices “computers”. These days we use many words instead of the word “computer”. We call it “smartphone”, “laptop”, “tablet”, etc. And we use those things everywhere. We even eat food by using our smartphone.
Scope Of Computer Science
As per the current trends, the career in computer science has gained a tremendous pace for years and today, the field is highly demanded.
There are a number of courses available in the market and if you want to start the course for getting a good job, then it is suggested to choose the right course for yourself.
There are different types, of courses, available for computer science education and one of the most important things that you have to keep in mind while choosing the best course is whether the course is right for you or not.
We all know that the role of a computer scientist is one of the most challenging jobs and it requires different skills and abilities. If you are looking for a well-paid job, then choosing the best course is of great importance for you.
In today’s era, you can make your career as a computer scientist with the help of the right training. To choose the right course for yourself, you must consider several things that are given below.
Knowledge of programming languages
The first thing that you need to consider is the language that you are going to learn. Most of companies require candidates who are fluent in programming languages, so it is advised to learn at least two programming languages. If you are a beginner, then it is suggested to start with Python, Java, C++, and JavaScript. It will help you to improve your skills and get trained in the latest technologies.
Knowledge of Computer architecture
If you want to make your career in this field, then you must keep in mind how much you have knowledge of Computer Architecture. If you are a novice, then you need to learn everything from scratch. If you already have knowledge of the computer architecture, then it will make your career easier and you will be able to get higher grades.
Advanced problem solving skills
If you want to become a successful computer scientist, then it is essential to possess advanced problem solving skills. This is one of the most important aspects that can differentiate you from other candidates. If you can solve an average problem, then you will not be considered a candidate.
Programming projects
You can make your career as a computer scientist if you can make your own projects. You will be required to write codes for different purposes and projects. In order to make your project successful, it is recommended to make it innovative.
Branches of computer science
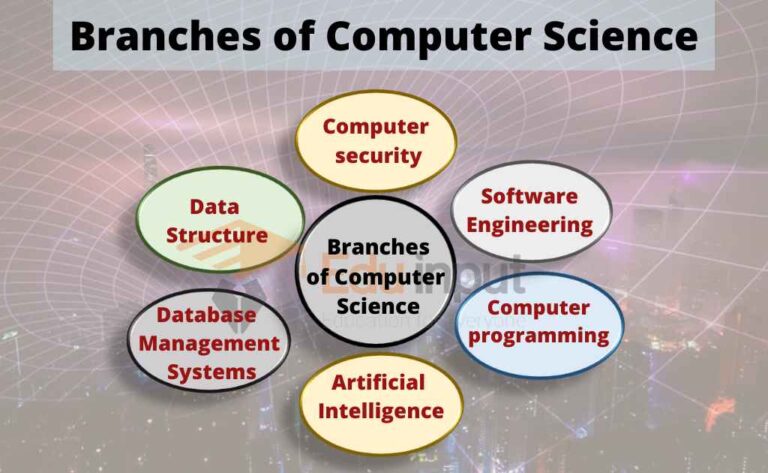
Computer Science is the study of the design of computers and computer systems. The study of computers and computing is referred to as computer science. The analysis of data structures, computer and network design, modeling data and information processes, and artificial intelligence are included.
A lot of mathematics, statistics, and probability are used in computer science. There is a lot of experimentation used to test hypotheses.
Artificial intelligence, computer systems and networks, information security, database systems, and human-computer interaction are some of the main areas of study of artificial intelligence. There are many different branches that artificial intelligence covers, from theoretical computer science to the applications of computer technology in the real world.
Software engineering
Software engineering is the branch of computer science that deals with the design, development, testing and maintenance of software applications.
Software developers write code to create applications. Software developers use programming languages and design software solutions for users.
Artificial Intelligence
Artificial intelligence is a branch of computer science that deals with techniques that mimic or even recreate the capabilities of the human mind. A new type of intelligent machine that can respond in the same way as humans is created by Artificial Intelligence. Artificial intelligence can find human wisdom. Humans will eventually be surpassed by artificial intelligence.
Programming languages
Programming languages are used by most other disciplines in order to function in computer science. The programmers translate the programming language into the computer’s language of choice. The study of programming languages and logic is focused on designing the languages and analyzing them. This study shows how to use the smallest amount of code in the languages to write complex programs.
Computer security
There is a discipline of computer science that deals with protecting information on computers. One of the things that can be included in this is the creation of software that is invulnerable to theft, destruction, fraud, or access by an unauthorized user. The part of computer security that protects the data is called computer security. It is a practice to translate information from its natural state into a hard- to-decipher pattern using a set of rule-based computations as well as using a set of algorithms to decode data.
Database Management Systems
Database Management Systems are the most used and popular area of computer science. People use this application to store data and information.
Topic Wise Computer Articles
Difference Between in Computer
Difference Between The Internet And World Wide Web (WWW)
Difference Between Input Devices And Output Devices
Difference Between Supercomputer And Mainframe Computer
Difference Between LCD and CRT
Difference Between RAM And ROM
Difference between Impact printer and Non-impact printer
Difference between low-level language and high-level language
Difference Between Spreadsheet And Word Processor
Difference Between DOS And Windows
Difference Between Source Code and Object Code
Difference Between Application and System Software
Basics of information technology
Mini Computers-Types of Mini Computers
Desktop Computer–Types of Desktop Computer
Supercomputers-Features, Advantages and Disadvantages of supercomputer
Optical Readers-OCR, OMR, MICR, And Barcode Reader
What is Computer Motherboard?-Types and History of Motherboard
What is Scanner in Computer?- Types of the scanner
What is SSD (Solid State Drive)?
What are Storage Devices?-Different Storage Devices
What is a Computer Mouse
The Computer System-SDLS and its Phases
What is Presentation Software?
History of Computer | Early Calculating Devices
What is Printer? | Different Types of Printers
Data and Information in Computer
5 Interesting Facts About Computers History
Software- Definition, types of Software
Abbreviation for Computer Science | IT Abbreviation
Generations of Computers- First to Fifth Generation of Computer
Information Network
Computer Network – Types of Computer Network
Computer Network and Network Topologies
Local Area Network(LAN)-Advantages and Disadvantages of LAN
What is a WAN Network? – Advantages and Disadvantages of Wide Area Network
Network Devices – Types of Devices of Computer Network
What is an Integrated Circuit?-Parts of ICs
What is Internet? – History of the Internet, Addressing Schemes
What are the Advantages of the Internet?
What are the Disadvantages of the Internet?
What is World Wide Web? – Components of World Wide Web
What is TCP/IP-History of TCP/IP, And How does TCP-IP work?
Essential Tips for Choosing Best Computer Network Service Provider
OSI Model-7 Layers of OSI Model
Physical Layer of OSI Model – Function of Physical Layer
Application Layer in OSI Model | Application Layer Protocols
Transport Layer of OSI Model | Session Layer of OSI Model
Computer Architecture
What is CPU?–Components of CPU
Expansion Bus-Types of Expansion Buses
Von Neumann Architecture-Fetch, Decode, And Execute Cycle of CPU
I/O Interface (Interrupt and DMA Mode)
5 Factors Effecting the Processing Speed
What is Cache Memory?-Levels of Cache Memory
What are Computer Ports?-Types of Computer Ports
What are CPU Registers?-Types of CPU Registers
Memory Units of Computer-Bit, Byte, Nibble, Word
Windows Operating System
Fundamentals of the Internet
What is Internet? – History of the Internet, Addressing Schemes
What are the Disadvantages of the Internet?
What are the Advantages of the Internet?
What is E-Commerce? – Roll of E-Commerce in Daily Life
Internet Service Provider(ISP)-Different Types of ISP
Search Engine – History of Search Engine
What is Web Browser – History of Web Browsers
Internet Services – Difference between Intranet and Extranet
Basics of database
What are Database-Types of Database
Components of Database | Advantages of DBMS over the File system
Database Management System-Advantages and Disadvantages of DBMS
Database Languages-Data Definition Language (DDL), Data Manipulation Language (DML)
What are Attributes in DBMS?-Types of Attributes in DBMS
Data Dictionary in DBMS–Types of Data Dictionary
Distributed Database Management System (DDBMS)–Advantages and Disadvantages
Distributed Database Design–Factors of DDBMS
Staged Database Design Approach-Steps of Database Design Approach
Degree of Relationship in DBMS-Unary, Binary, Ternary, and N-ary (n degree) Relationship
Introduction to C/C++
What are Keys in DBSM?–Types of Keys
History of C Language – Advantages and Disadvantages of C Language
Programming Languages | Language processor
High-Level Programming Language-Popular High-level languages
Debugging in Turbo C++ | Different types of Error in C/ C++
Structured Programming Technique-Advantages and Disadvantages
Problem Solving Techniques in Computer Science
Introduction to Flowchart | Difference between Flowchart and Algorithm
Variable in C Language–Variable Declaration, And Variable Initialization
What Are Constants In C/C++?-Literal Constant, Symbolic Constant
Assignment Operators in C++ | Compound Assignment Operators in C++
Increment and Decrement Operators in C++
Relational Operators in C++ | Relational Expressions
Logical Operators in C++ | Different Logical Operators
Arithmetic Operator in C++
Operators in C++ | Unary and Binary operators
C++ Data Types-int, float, char, double, bool
Functions in C/C++ | Advantages of Functions in C/C++
What are Escape Sequences in C Language?
Applications and uses of computer
Uses Of Computers For Office Automation
Uses of Computers in Communication
Use of Computers in the Field of Chemistry
Applications of Computer in the Agriculture
Use of Computer in the Defense Department
Use of Computers in Education Field
Use of Computers in Education Field
Applications Of Computer In Different Fields
Computers are used in different fields for different purposes.
In Education Department
Computers play an important role in the education sector. They are used for online classes, examinations, e-books, and tutoring. They help to increase the use of audio-visual aids in education.
In Banks
Computers play a vital role in the banking sector as they store customer information and are used to conduct various transactions such as money withdrawals and deposits via ATMs. By extensively using computers, banks have been able to reduce manual errors and expenses significantly.
At Homes
There are many different uses for computers at home. Some people use them to listen to music, watch movies, or even keep track of their finances. Others use them for work or school purposes.
In Medical Field
Computers play an important role in the medical field. They are used to provide better care for patients, and they are also used during surgery. They can keep track of employees and doctors, keep records of medicine, and perform CT scans and x-rays.
In Businesses
A computer is an essential tool for businesses, big and small. It can be used for a variety of tasks, from creating and printing documents to keeping records of projects. Having a computer in the office can help improve efficiency and productivity, and it can also be a great way to stay organized.
In Chemistry
In the field of chemistry, computers are used for a variety of tasks such as research, online publication, and testing.
In Agriculture
Computers have become an important aspect of agricultural productivity, as the industry increasingly relies on technology to streamline various processes. Farming apps help farmers keep track of their inventory, soil conditions, and crop yield, while GPS-enabled equipment helps with mapping and navigation. In addition, automated irrigation systems and weather-tracking software help farmers optimize their water usage and reduce wastage.
In Offices
In the office, we use a computer for a variety of tasks such as creating CVs and other documents, keeping track of employees, and managing customer records.
The computer has made it possible for people all over the world to communicate with each other easily. With email, WhatsApp, Instagram, Facebook, and many other social media apps, we can connect with anyone no matter where they are in the world. In a way, the computer has turned the globe into one big village.
In Defense Department
Computers are utilized in the defense department to create new weaponry and store data on weaponry and soldiers. They play a vital role in organizing different aspects of a soldier’s life, such as monitoring salaries and wages, meal plans, and schedules for training and other events. Having this organized makes it easier for the soldiers to focus on their duties rather than having to worry about other tiny details.
Future of Computer Science
The future of computing will continue to progress at a rapid pace. The amount of data being produced by the human race is increasing exponentially. And, we need more and more sophisticated ways to analyze the data.
The demand for computing is high and is likely to remain high. Computers and the data they produce will become even more useful in the future.
Related FAQs
What does computer science do?
Computer science is the study of developing software and software systems. It uses mathematical models to analyze data, security, and algorithms. Computer scientists define the principles that all software is based on.
Is computer science just coding?
Although computer science and coding may seem very similar, they are in fact two different concepts. Where computer science focuses on the theory of what computers can do, coding is the act of putting this theory into practice. So, while a background in computer science may help you with coding, it is not an essential requirement.
Is computer science is a good career?
If you’re looking for a degree that will lead to an in-demand, high-paying career, look no further than computer science. In the next decade, graduates with a computer science degree will have some of the best job prospects of any degree, with careers in fields like software engineering, artificial intelligence, data science, and more.
So if you’re looking for a degree that will set you up for success, look no further than computer science.
Who is called the father of computer?
Charles Babbage is called the father of computer. He invent the difference engine, on which all the computer based.
What are the applications of computers?
Computers have become a staple in our homes for many reasons such as paying bills online, streaming movies and television, getting tutored from the comfort of our homes, accessing social media, playing video games, and browsing the internet.
Difference between Twisted pair cable, Coaxial cable, and Fiber optics cable
Twisted pair cable, coaxial cable, and fiber optic cable are communication media. The main difference between the twisted pair cable, coaxial cable, and fiber optic cable is, fiber optic cable is made of glass or plastic fibers and is used for transmitting data over long distances at high speeds.
Twisted pair cable is made of two copper wires that are twisted together and are commonly used in Ethernet networks. Coaxial cable is made of copper wire surrounded by an insulating material and is often used in cable television networks.
Twisted pair cables
Twisted pair cables are an essential part of any home or office setup because they transfer data at high speeds without any interference. A twisted pair cable consists of two wires twisted together to provide conductivity between the two ends of the wire.

Twisted pair cables are commonly used in telephone networks, computer networking, and data communications.
Coaxial Cable
Coaxial cable is a combination of both fiber optics and copper wire. It is commonly used in television transmission systems. Coaxial cable is composed of three parts: the center conductor (or inner conductor), the insulator, and the outer conductor.

Fiber Optics
Fiber optics is a communication technology that uses glass fibers to transmit data over long distances at high speeds. These cables have been around since the early 1900s, but they were not widely adopted until the 1980s.

Fiber optics is now being used in many different industries including telecommunications, computer networking, and medical equipment.
Twisted pair cable vs Coaxial Cable vs Fiber optic cable
The main differences between twisted pair cable, coaxial cable, and fiber optic cable are as follows:
| Twisted pair cable | Coaxial Cable | Fiber Optic cable |
| Its bandwidth is low. | Its bandwidth is very high. | Its bandwidth is high. |
| It is inexpensive. | It is more expensive than twisted pair cable. | It is very costly. |
| It supports a low data rate. | It supports a high data rate. | It supports a very high data rate. |
| It is affected by external magnetic material. | It is affected by the external magnetic material | It is affected by the external magnetic material |
| Twisted pair cable has low noise immunity. | Coaxial cable has higher noise immunity as compared to twisted pair cable. | Fiber optical cable has higher noise immunity. |
| It is easy to install. | It is easy to install. | It isn’t easy to install. |
| Attenuation is low | The attenuation is very high. | The attenuation is very low. |
What are Signals in Computer?Forms of Signals
The signal is an electromagnetic or light wave that represents data. Signals in computers are sent through a communication medium in order to conduct data transmission. Signals are created by sending an electric current through the medium.
The receiving device then goes through the same process, which turns the current into sound, image, or text. Data signals can be man-made or natural. Signals can also be big and small. Big signals are referred to as ‘broadband’ signals since they have a large bandwidth.
Forms of signals
The signals are in two forms
- Digital Signals
- Analog Signals
Digital Signals
A digital signal is a series of ones and zeros that represent information. A digital signal can be represented by a voltage level or current flow. In electronics, a digital signal is often represented by a voltage level. When a voltage level changes, it represents a 1 or 0.
There are two types of digital signals: positive and negative. Positive digital signals have a higher voltage than negative digital signals.
All data communication between computers occurs in digital form. This is because computers can only understand and work with digital signals. The following figure represents a high voltage signal as a 1 and a low voltage signal as a 0.
Analog Signals
An analog signal is an electrical signal that takes the form of a wave. This wave is known as a carrier wave. The most common medium used for transmitting analog data is a telephone line. However, light, sound, radio waves, and microwaves are also examples of analog signals.
Characteristics of Analog Signal
Two characteristics of analog signals are as follows.
Frequency
Frequency is how often a wave occurs during a specific time interval. Frequency refers to the number of times something happens per second. In audio, frequency refers to the pitch of the sound.
A higher frequency means a higher-pitched sound while a lower frequency means a lower-pitched sound. When we talk about frequency in electronics, it refers to how often a voltage changes (or current flows).
Amplitude
The height of a wave within a given period of time is known as amplitude. Amplitude is how much something is changing. Amplitude refers to the amount of power being sent out. If we have a sine wave, then its amplitude would be at its peak. If we had a square wave, then its amplitude is at 0.
What is TCP/IP-History of TCP/IP, And How does TCP-IP work?
The Internet is a very powerful tool that helps to connect millions of people across the globe. the Internet is a global system of interconnected computer networks that use the Internet Protocol (IP) as the network layer protocol.
The TCP/IP (Transmission Control Protocol/Internet Protocol) is a suite of protocols used for communication over the Internet.
TCP/IP protocols are the fundamental building blocks of the Internet. The TCP/IP is a connectionless, best-effort, and unreliable networking protocol suite that runs on top of the Internet Protocol (IP) network layer.
TCP/IP defines two essential protocols: the Transmission Control Protocol (TCP) and the Internet Protocol (IP). TCP/IP is a core set of protocols in the Internet protocols suite.
TCP/IP defines the rules and conventions of the Transmission Control Protocol (TCP), the User Datagram Protocol (UDP), the Internet Control Message Protocol (ICMP), and the addressing and routing protocols. It also provides a common architecture for computers and devices to communicate over the Internet.
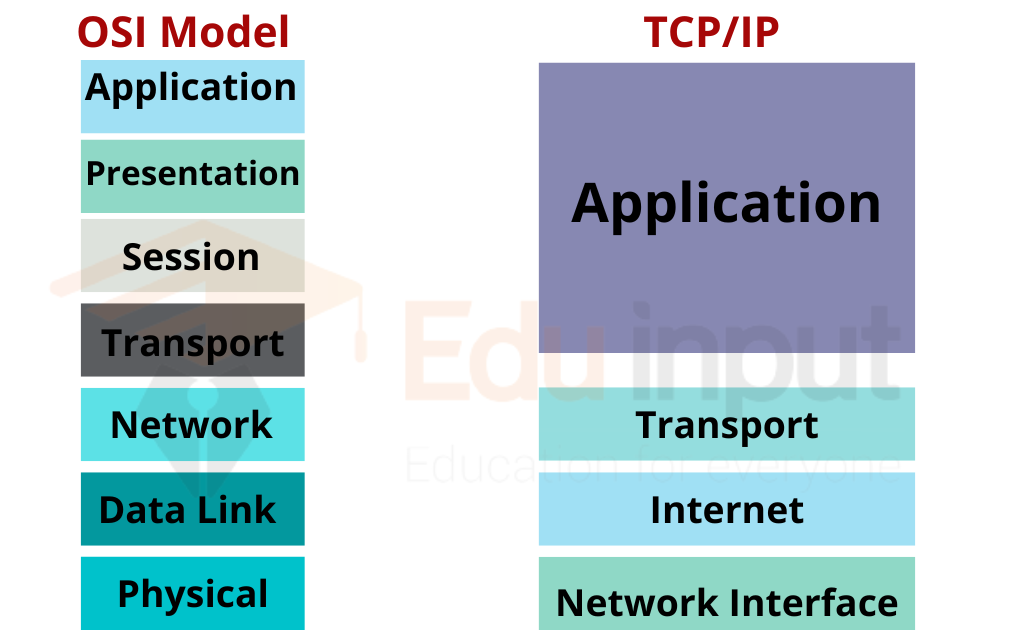
In short, the TCP/IP is a standard set of protocols and the most widely used protocol on the Internet. And if you are wondering what is the difference between IP and TCP.
IP (Internet Protocol)
Internet Protocol (IP) is the network layer protocol. It provides the services required for delivering datagrams, including datagram encapsulation and de-encapsulation, fragmentation and reassembly, datagram sequencing, and flow control.
TCP (Transmission Control Protocol)
The Transmission Control Protocol (TCP) is a transport layer protocol that ensures the reliable exchange of information between a host and its environment. It provides full-duplex, sequential, connection-oriented, reliable, and error-free data transmission. The TCP is a component of the TCP/IP suite of protocols and is used in the client-server model of computing.
History of TCP/IP
The TCP/IP model was developed in 1970 by the defense advanced research projects agency (DARPA) which was the branch of the research department of U. S. It is invented by two scientists Vint Cerf and Bob Khan, who was working on the data communication.
Four layers of the TCP/IP model
TCP/IP is divided into four layers, which include the specific protocol or rules. All layers work collectively for the transfer of data from one layer to another.
- Application layer
- Transport layer
- Internet layer
- Network Access layer
How does TCP-IP work?
TCP-IP is a technology that is used to share information between computers. The Internet is built using TCP-IP. It is the basic communication technology of the Internet.
The Internet uses IP addresses and IP protocols to transfer data between the servers and the end user. The IP is nothing but the unique identifier of the device. Every device that is connected to the internet has its own IP address.
This is all about TCP/IP. If you have any questions about TCP/IP, you can share them in the comment section below.
Difference Between Tree and Star Topology
The main difference between tree and star topology is their structure. Tree topology has a hierarchical structure with devices connected in layers, like branches on a tree. The main “root” node connects to smaller hubs, making it ideal for large networks with many sections. Star topology has a centralized structure where all devices connect to a single hub. It’s easy to manage, but the network fails if the hub fails.
Star Topology
In star topology, each device is connected directly to a central hub (like a Wi-Fi router). All communication happens through this hub.
Tree Topology
Tree topology has a central root node that connects to other devices in a branching, tree-like structure. It’s similar to a family tree with main and smaller branches.
Star Topology vs Tree Topology
The following comparison table shows the difference between tree and Star Topology:
| Feature | Star Topology | Tree Topology |
| Structure | Central hub with devices connected to it. | Hierarchical structure with a root node and branches. |
| Ease of Setup | Simple and easy to set up. | More complex because of multiple layers. |
| Scalability | Works well for small to medium-sized networks. | Works better for large networks with many sections. |
| Failure Impact | If the hub fails, the whole network fails. | If a branch or root node fails, only that section is affected. |
| Example | Wi-Fi network in a classroom or home. | A large office network with multiple departments. |
FAQs
Are tree and star topology the same?
No. The Star has a single hub, while the tree is hierarchical with multiple levels. The tree is more scalable; the star is simpler.
Which is the fastest topology?
Star topology is the fastest because each device connects straight to a main hub, making data move quickly.
Who uses star topology?
Hospitals, Schools, colleges, Banks and airports
Which topology is easy?
Star topology is the easiest because each device connects directly to a central hub, simplifying setup and troubleshooting.
Advantages and Disadvantages of Mesh Topology
The main advantage of mesh topology is its high reliability, as data can travel through multiple alternate paths if one connection fails, keeping the network functional. However, its main disadvantage is the high cost, as setting up and maintaining the network requires many cables and connections, making it expensive.
Advantages of Mesh Topology
Here are the advantages of the mesh topology
1. Fault Tolerance
One of the most significant advantages of mesh topology is its ability to remain operational even if some connections fail. Since each node is connected to every other node, there are many alternate paths for data to travel, ensuring the network doesn’t break down quickly.
2. High Data Traffic Handling
Mesh topology can handle large amounts of data because there are multiple paths for data to take. This helps prevent congestion and ensures smooth communication between devices.
3. Scalability
It is easy to add more devices to a mesh network. New nodes can be connected without interrupting the existing network, making it highly scalable.
4. Robustness
Each node in a mesh network acts as a router, helping to improve the reliability and efficiency of data transmission. Even if one device fails, the rest of the network can continue working.
5. No Centralized Control
In mesh topology, there is no central device controlling the network, which reduces the risk of a single point of failure. This makes the network more secure and less vulnerable to attacks.
Disadvantages of Mesh Topology
Despite its benefits, mesh topology also has some critical drawbacks
1. Costly Implementation
Setting up a mesh network can be expensive because each device needs to be connected to every other device, which requires more cables and hardware. This makes mesh topology costly to install.
2. Complex Installation and Maintenance
Installing and maintaining a mesh network can be complicated. With so many connections between devices, it can be challenging to set up and manage the network.
3. Power Consumption
Since every node must be active, mesh networks tend to consume more power. This can lead to higher energy costs compared to simpler network topologies.
4. Redundant Connections
With so many connections between devices, mesh topology can result in excess wiring. This can make the network design more complicated than necessary and lead to wasted resources.
FAQs
Why is mesh better than star topology?
Mesh topology is better because it’s more reliable and has multiple data paths, but it’s more complex and costly.
What is the full form of mesh?
Mesh doesn’t have a full form. It refers to a network with multiple connections between devices.
What is the best example of mesh topology?
The Internet is the best example of mesh topology.
What is the benefit of a mesh network?
The mesh network is reliable because data finds other paths if one fails.


